Cryptographic hash function facts for kids
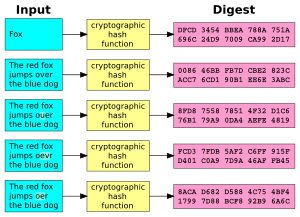
A cryptographic hash function is like a special digital fingerprint for information. It takes any piece of data, like a message or a file, and turns it into a short, fixed-size code. This code is often called a 'hash value', 'message digest', or 'digital fingerprint'. Think of it as a unique ID for your data.
An ideal hash function has three main superpowers:
- It's super easy to create a hash for any data you have.
- It's incredibly hard for computers to guess the original data just by looking at the hash.
- It's almost impossible for two different pieces of data to have the exact same hash. Even a tiny change in the original data will create a completely different hash.
Contents
What are Hash Functions Used For?
Hash functions with these special powers are used for many important things, especially in keeping information safe.
Checking Data Safety
One big use is to check if data has been changed. Imagine you send a secret message. You can also send its hash. The person receiving the message can then create a hash of what they got. If their hash matches yours, they know the message hasn't been tampered with. This helps make sure messages are delivered correctly and securely.
Digital Signatures and Security
Hash functions are also key for digital signatures. A digital signature is like your real signature, but for online documents. It proves that you sent the message and that it hasn't been changed. They are also used for authentication, which means proving you are who you say you are, like when you log into a website.
A hash function takes a string of any length and makes a fixed-length "signature" for it. Someone who knows the hash value cannot figure out the original message. But the person who knows the original message can prove that the hash value came from that message.
How a Hash Function Should Work
A good cryptographic hash function should act like a random process, even though it always gives the same result for the same input. It should be very efficient to calculate.
A cryptographic hash function is considered "unsafe" if it's possible for computers to do either of these things:
- Find a new message that creates a specific hash value.
- Find two different messages that create the exact same hash value. This is called a "hash collision".
If someone can do either of these, they could trick systems. For example, they could replace a real message with a fake one that has the same hash, making it look legitimate.
Ideally, it should be impossible to find two different messages whose hashes are similar. Also, you wouldn't want an attacker to learn anything useful about a message just from its hash. Of course, the attacker learns the hash itself, which lets them know if the same message appears again.
Popular Hash Functions
For a long time, two common hash functions were MD5 and SHA-1. However, around 2005, experts found some weaknesses in them. These weaknesses showed that it might be possible for clever attackers to break them. Because of this, stronger hash functions were recommended.
In 2007, the National Institute of Standards and Technology (a US government agency) held a contest. They wanted to find a new, super strong hash function. The winner of this contest was named SHA-3. It is now an official US government standard for secure hashing.
Related pages
See also
 In Spanish: Función hash criptográfica para niños
In Spanish: Función hash criptográfica para niños

