SP-network facts for kids
In the world of secret codes, an SP-network (short for Substitution–Permutation network) is a special way to mix up information. It's used in many modern secret-keeping methods, like the AES (Advanced Encryption Standard) cipher. Think of it as a recipe for turning a normal message into a secret one, making it very hard for anyone else to read without the right key.
Contents
What is an SP-Network?
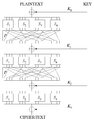
An SP-network takes your original message, called the plaintext, and a secret key. It then puts them through several steps, or "rounds," to create a secret message, called the ciphertext. These steps involve two main parts:
- S-boxes (Substitution boxes)
- P-boxes (Permutation boxes)
These S-boxes and P-boxes change small pieces of the message. They use operations that computers can do very quickly, like XOR (exclusive or) and moving bits around. A special part of the key, called a "round key," is added in each step to help mix things up even more.
How Does it Work?
Imagine you have a message. An SP-network works by doing these steps over and over:
- First, it uses S-boxes to swap out small groups of bits for other groups.
- Then, it uses P-boxes to rearrange all the bits.
- After that, it mixes in a "round key" from your secret key.
This process is repeated many times, making the message more and more scrambled.
To get the original message back, you just do these steps in reverse. You use the opposite of the S-boxes and P-boxes, and apply the round keys in the opposite order.
S-boxes: Swapping Bits
An S-box takes a small group of bits as input and swaps them for a different group of bits. For example, it might take 4 bits and turn them into 4 new bits. This swap must be unique, meaning each input always gives a specific output. This makes sure you can always reverse the process to get the original bits back.
A good S-box has a cool trick: if you change just one bit in its input, about half of its output bits will change. This is called the "avalanche effect." It means even a tiny change in the original message creates a huge change in the secret message.
P-boxes: Mixing Bits Around
A P-box takes all the bits that came out of the S-boxes in one step and shuffles them around. It's like taking a deck of cards and rearranging them completely. The goal of a good P-box is to spread out the bits from each S-box to as many different S-boxes as possible in the next step. This helps to mix the information across the entire message.
Round Keys: Adding the Secret
At each step, a "round key" is mixed into the message. This round key is made from your main secret key. It's usually combined with the message bits using an operation like XOR, which is a simple way to combine numbers in computer code.
Why SP-Networks are Strong
Alone, an S-box is like a simple substitution cipher (swapping letters). A P-box is like a simple transposition cipher (rearranging letters). But when you put them together in an SP-network with many alternating rounds, they become very strong. This strength comes from two important ideas: diffusion and confusion.
Diffusion: Spreading Changes
Diffusion means that if you change just one bit in your original message, that change will spread out and affect many bits in the final secret message. Here's how it works:
- You change one bit in the original message.
- That bit goes into an S-box, which changes several output bits.
- The P-box then spreads these changed bits to many different S-boxes in the next step.
- This continues for several rounds, making the changes spread across the entire message.
By the end, the secret message looks completely different from what you'd expect if you only changed one bit. This makes it very hard for someone to guess what the original message was, even if they know a tiny part of it.
Confusion: Hiding the Key
Confusion means that the relationship between the secret key and the secret message is very complex and hard to figure out.
- If you change just one bit in the secret key, it changes several "round keys."
- Each change in a round key then spreads out and affects many bits in the secret message.
This makes it extremely difficult for an attacker to work backward from the secret message to figure out your secret key, even if they have examples of original messages and their secret versions.
Images for kids