Firewall (computing) facts for kids
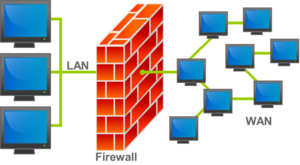
A firewall is like a security guard for your computer network. It's a system that watches and controls all the information (called network traffic) trying to come into or go out of your network. It uses special rules to decide what information is allowed and what isn't. Think of it as a barrier between your safe, trusted network (like your home Wi-Fi) and an untrusted network (like the big Internet). Firewalls can protect a whole network or just a single computer.
Contents
How Firewalls Started
The word firewall first meant a real wall built to stop a fire from spreading between buildings. Later, it described things like the metal sheet that separates a car's engine from the passengers. In the 1980s, when the Internet was becoming popular, people started using the word for network security.
Before firewalls were common in computers, routers were used in the 1980s. Routers already separated different parts of a network, so they could also help filter the data passing through them.
The idea of a computer firewall might have even been inspired by the 1983 movie WarGames. In the movie, a programmer talks about a "firewall" in a computer system.
One of the first successful firewalls for businesses was called the PIX Firewall. It was created in 1994 by a company called Network Translation Inc. The PIX Firewall helped companies connect their private networks to the public internet safely, even when there weren't many internet addresses available. It quickly became very popular. In 1995, Cisco Systems bought Network Translation Inc. to get the PIX technology. The PIX was a very important firewall for Cisco for many years.
Different Kinds of Firewalls
Firewalls can be grouped into two main types: network-based or host-based.
- Network-based firewalls are placed between two or more networks. For example, they might sit between your local network (LAN) and the wider internet (WAN). Their main job is to control how data flows between these connected networks. These firewalls can be special devices (hardware), software running on a regular computer, or even virtual versions running in a cloud. They might also offer other services, like helping devices get IP addresses or setting up secure connections.
- Host-based firewalls are installed directly on a single computer or server (the host). They control the network traffic specifically for that one machine. This can be a part of the computer's operating system or a separate security program.
Packet Filters
The very first type of network firewall was called a packet filter. It checked individual pieces of data, called "packets," as they moved between computers. The firewall had a list of rules, like a guest list, that told it which packets to look at and what to do with them. If a packet didn't match any rule, the firewall would usually just quietly throw it away.
Packets could be filtered based on where they came from (source IP address), where they were going (destination IP address), the type of communication (TCP or UDP), or the specific port number being used. In the past, most internet communication used specific ports for things like web browsing (port 80), email (port 25), or file transfers. This made it easier for firewalls to tell what kind of traffic was passing through.
Engineers at Digital Equipment Corporation (DEC) first wrote about packet filter firewalls in 1987. Later, researchers at AT&T Bell Labs also worked on and improved these early packet filtering systems.
Tracking Connections
Around 1989-1990, new types of firewalls were developed. These were called circuit-level gateways.
These newer firewalls could do everything the first ones did, but they also remembered ongoing conversations between computers. They kept track of which IP addresses were talking to each other and which port numbers they were using. This allowed them to understand the whole exchange of information, not just individual packets.
Application Layer Firewalls
In 1993, a new kind of firewall was released called the Firewall Toolkit (FWTK). This firewall was special because it could understand specific applications and protocols, like File Transfer Protocol (FTP) for transferring files, Domain Name System (DNS) for looking up website names, or Hypertext Transfer Protocol (HTTP) for web browsing.
The main benefit of this "application layer" filtering is that it can tell if an application is trying to use a strange port or if a normal protocol is being misused. It can also help manage security for things like encrypted DNS and virtual private networks.
Since about 2012, even more advanced firewalls, called next-generation firewalls, can inspect traffic even more deeply at the application level. They can do things like:
- Filter websites you visit (web filtering).
- Stop attacks (intrusion prevention systems).
- Manage who is using the network (user identity management).
- Protect web applications.
- Check content for threats.
- Inspect encrypted traffic (TLS Inspection).
Protecting Endpoints
Endpoint-based application firewalls work by deciding if a program on your computer should accept a connection. They check the program's ID against a set of rules for that program. These firewalls often "hook into" the way programs connect to the network (called socket calls) to filter connections between the program and the network.
Firewall Rules and Policies
At the heart of every firewall are its rules, also known as firewall policies. These are the specific instructions that tell the firewall what information (traffic) to allow or block as it crosses the network's borders.
Firewall rules work by checking network packets against certain security requirements. A network packet, which carries data, must match specific details defined in a rule to be allowed through. These details often include:
- Direction: Is the traffic coming in or going out?
- Source: Where did the traffic start (e.g., an IP address, a range of addresses, or a network zone)?
- Destination: Where is the traffic trying to go (e.g., an IP address, a range, or a network zone)?
- Port: Which network port is being used (e.g., port 80 for HTTP web traffic)?
- Protocol: What type of network communication is it (e.g., TCP, UDP, ICMP)?
- Applications: What specific application is using the traffic?
- Action: What should the firewall do? Allow it, block it, or check it more closely?
Network Zones
Zones are like separate sections within a network that group devices with similar security needs. By dividing a network into zones, such as "LAN" (your local network), "WAN" (the internet), "DMZ" (a special zone for public servers), or "Wireless" (for Wi-Fi devices), network managers can set different rules for each section. Each zone has its own level of trust, and specific firewall rules control what data can enter or leave it.
A common setup is to allow all traffic from your local network (LAN) to the internet (WAN), but to block all traffic trying to come from the internet (WAN) into your local network (LAN) unless it's specifically allowed.
Network Services
In networking, services are specific functions that usually use a certain network port and protocol. For example, web traffic uses HTTP/HTTPS on ports 80 and 443. File transfer uses FTP on port 21, and email uses SMTP on port 25. Services are what make applications work.
Controlling access to services is very important for security because services are often targets for attacks. Firewalls use rules to say which services should be available, to whom, and in what situations. For instance, a firewall might block incoming FTP requests to stop unauthorized file uploads but allow outgoing HTTPS requests so you can browse the web.
Network Applications
Applications are the software systems that people use on a network, like web browsers, email programs, or online games. In network security, applications are important because different types of traffic can have different security risks.
Firewall rules can be made to identify and control traffic based on the specific application that is sending or receiving it. By understanding applications, firewalls can allow, block, or limit traffic for certain apps based on a company's rules. This helps protect against threats from apps that might be vulnerable or unwanted.
An application can be a group of services, or it can be identified by looking deeply into the data itself.
User ID
Using firewall rules based only on IP addresses can be tricky because people move around and use different devices. This is where "User ID" becomes very helpful.
User ID allows firewall rules to be based on who the person is, not just their computer's IP address. This makes security much better because it gives more precise control over who can access certain network resources, no matter where they are connecting from or what device they are using.
User ID technology usually works with directory services like Active Directory, LDAP, or RADIUS. These services link a user's login information to their network activities. By doing this, the firewall can apply rules that match user groups (like "Students" or "Teachers"), roles, or individual user accounts, instead of just relying on where their computer is located on the network.
Example: Using User ID in Firewall Rules
Imagine a school that wants to stop students from accessing a social media server. They can create a firewall rule using User ID to make this happen.
- Setting up the Directory Service: First, the firewall needs to be set up to talk to the directory service that holds information about user groups, like an Active Directory server.
- Identifying Users: The firewall connects network traffic to specific user IDs by checking login records. When a user logs in, the firewall links that login to the user's IP address.
- Defining User Groups: In the firewall's settings, you create user groups based on the directory service. For example, you might create a group called "Students."
- Creating the Firewall Rule:
- Source: User ID (e.g., the "Students" group)
- Destination: The IP addresses of the social media servers
- Service/Application: Allowed services (e.g., HTTP, HTTPS)
- Action: Deny (block access)
- Setting a Default Allow Rule:
With this setup, only users who log in and are identified as members of the "Students" group will be blocked from accessing social media servers. All other traffic starting from the school's network will be allowed.
Common Firewall Log Types
Firewalls keep detailed records of everything they do. These records, called logs, are very important for understanding what's happening on the network and for security.
- Traffic Logs: These logs record details about all the data moving across the network. This includes where the data came from, where it was going, the port numbers and protocols used, and what the firewall did (allowed, blocked, or rejected it). They help network managers understand communication patterns and fix problems.
- Threat Prevention Logs: These logs specifically capture information about security threats. This includes alerts from systems that stop intrusions, antivirus events, and other threat detections. They are vital for finding and responding to possible security breaches.
- Audit Logs: These logs record changes made to the firewall's settings by administrators. They are important for tracking who made what changes, which helps with security checks and making sure rules are followed.
- Event Logs: These are general logs that capture many different events happening on the firewall. They help administrators monitor and fix any unusual activities or performance issues.
- Session Logs: These logs provide information about active network connections, including when they started and ended, how much data was transferred, and which user or device was involved. They are useful for watching network connections in real-time and finding unusual activities.
- DDoS Mitigation Logs: These logs record events related to Distributed Denial of Service (DDoS) attacks, including actions the firewall took to protect the network. They are critical for quickly identifying and stopping DDoS attacks.
- Geo-location Logs: These logs show the geographic locations of network connections. This can be useful for monitoring and controlling access based on where people are connecting from, adding another layer of security.
- URL Filtering Logs: These logs record information about web traffic and which websites are allowed or blocked. They help organizations manage internet access and make sure people are following acceptable use policies.
- User Activity Logs: These logs capture information specific to users, such as when they log in or out, and their network traffic patterns. They help track user behavior and find potential security problems involving specific users.
- VPN Logs: These logs contain information about Virtual Private Network (VPN) connections, including when they connect or disconnect, and any VPN-related errors. They are important for making sure VPN connections are secure and working well.
- System Logs: These logs provide information about the firewall system's overall health, status, and configuration changes. This includes logs about high availability (HA) setups and software updates. They are essential for keeping the firewall working correctly.
- Compliance Logs: These logs specifically record events that are important for meeting regulatory requirements. They help organizations show that they are following industry standards or legal rules during audits.
Setting Up a Firewall
Setting up a firewall can be tricky and sometimes mistakes can happen. If a firewall isn't set up correctly, a network might face security problems.
Firewall rules are usually set up based on the type of network (like a public Wi-Fi network or a private home network). These rules either block or allow access to help prevent attacks from hackers or harmful software.
See also
 In Spanish: Cortafuegos (informática) para niños
In Spanish: Cortafuegos (informática) para niños
- Air gap (networking)
- Distributed firewall
- DMZ (computing)
- Firewall pinhole
- Firewalls and Internet Security
- Golden Shield Project
- Intrusion detection system
- Mobile security § Security software
- Windows Firewall
 | Janet Taylor Pickett |
 | Synthia Saint James |
 | Howardena Pindell |
 | Faith Ringgold |