IEEE 802.1X facts for kids
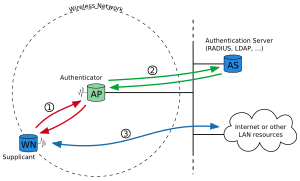
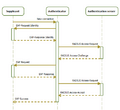
IEEE 802.1 is the name for a number of high-level protocols for computer networks. In this context, IEEE 802.1X helps secure such a network. It defines methods to authenticate devices and to authorise the access to certain resources. A dedicated server checks information received from a "supplicant". Depending on the result of the check, access to the given resource is granted or denied.
- IEEE standard can be retrieved at no charge through the GetIEEE802 program: [1]
Images for kids
See also
 In Spanish: IEEE 802.1X para niños
In Spanish: IEEE 802.1X para niños

All content from Kiddle encyclopedia articles (including the article images and facts) can be freely used under Attribution-ShareAlike license, unless stated otherwise. Cite this article:
IEEE 802.1X Facts for Kids. Kiddle Encyclopedia.