Meet-in-the-middle attack facts for kids
The Meet-in-the-middle attack is a clever trick used in cryptography, which is the science of secure communication. Imagine you have a secret message that has been encrypted not once, but twice, using two different secret keys. You might think this makes it super secure, right? This attack shows that it's not as strong as it seems.
This attack works by trying to "meet in the middle" of the encryption process. Instead of trying to guess both keys at the same time, which would take a very long time, an attacker works from both ends. They encrypt the original message with all possible first keys. At the same time, they decrypt the final encrypted message with all possible second keys. When the results from both sides match, they have likely found the correct keys!
This idea was first thought of by Whitfield Diffie and Martin Hellman in 1977. They were looking at ways to make block ciphers (a type of encryption) stronger. People thought that if you encrypted data twice with two different keys, it would be much, much harder to break. For example, if one key had 'n' possible combinations, two keys would seem to have 'n' times 'n' combinations. But Diffie and Hellman showed that this attack could break the double encryption much faster than expected.
How the Attack Works
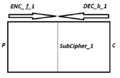
Let's say you have an original message, called P (for plaintext), and the final encrypted message, called C (for ciphertext). The message was encrypted like this:
- First, P was encrypted with Key 1 (let's call it K1) to get an intermediate message.
- Then, this intermediate message was encrypted with Key 2 (K2) to get C.
The attacker knows P and C. Here's what they do:
- Step 1: Encrypt from the start. The attacker takes the original message P. They try encrypting it with every single possible Key 1. They save all these results in a list.
- Step 2: Decrypt from the end. At the same time, the attacker takes the final encrypted message C. They try decrypting it with every single possible Key 2. They save all these results in another list.
- Step 3: Find a match. The attacker then looks for any results that appear in both lists. If a result from Step 1 matches a result from Step 2, it means they've found a potential pair of Key 1 and Key 2 that works!
To make this faster, the attacker often stores the first list in a special computer memory called a "lookup table." This allows them to quickly check if any of the decrypted results from Step 2 are already in the first list.
Why It's Faster
You might think that breaking double encryption would take a huge amount of time, like trying every combination of two keys. If each key has 'n' possible values, you might expect to try 'n' multiplied by 'n' combinations.
However, the Meet-in-the-middle attack is much quicker. It only takes about twice the time it would take to break a single encryption. This is because the attacker is doing two separate searches (one for Key 1, one for Key 2) instead of one combined search. The main cost is the computer memory needed to store the list of results from the first step.
Once a possible pair of keys is found, the attacker can test them on another known message and its encrypted version to make sure they are the correct keys.
Related pages
- Birthday attack
Images for kids
See also
 In Spanish: Ataque Meet-in-the-middle para niños
In Spanish: Ataque Meet-in-the-middle para niños
 | William Lucy |
 | Charles Hayes |
 | Cleveland Robinson |