Public key certificate facts for kids
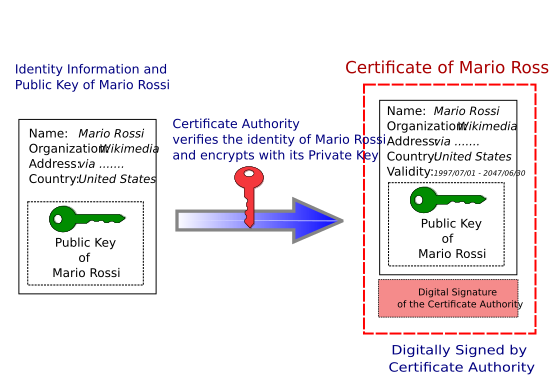
A public key certificate (also called a digital certificate) is like an electronic document that proves a public key is real. Think of it as a digital ID card for a public key. This certificate contains details about the key and its owner. It also has a digital signature from someone who checked and approved the certificate. This checker is called the issuer.
If your computer trusts the issuer's signature, it knows the key is valid. Then, your computer can talk safely with the key's owner. For example, when you visit a website, a certificate helps make sure you're connecting to the right place. This is a big part of HTTPS, which keeps your web browsing secure.
Often, the issuer of a certificate is a certificate authority (CA). A CA is usually a company that issues these digital IDs. If a key is ever stolen or misused, the certificate can be canceled (or revoked). The most common way these certificates are set up is called X.509.
Contents
What are Digital Certificates Used For?
Digital certificates help make sure that online communication is safe and trustworthy. They are used in many ways to prove who someone or something is online.
Keeping Websites Secure (TLS/SSL Server Certificates)
When you visit a website, the Transport Layer Security (TLS) protocol (or its older name, Secure Sockets Layer (SSL)) helps keep your connection safe. This protocol makes sure that your computer and the website's server can talk securely.
The website's server shows a digital certificate to prove it's the real website. Your computer then checks two main things:
- Does the certificate's name match the website you are trying to visit?
- Has a trusted certificate authority signed the certificate?
If these checks pass, your computer can create a secure, encrypted connection with the website. This is why you see "https://" in front of secure website addresses. Websites that are open to the public, like online stores, get their certificates from trusted companies called public certificate authorities.
Identifying Users (TLS/SSL Client Certificates)
Client certificates help prove who you are when you connect to an online service. For example, they can control who gets access to certain parts of a website. Since these services are often for people, client certificates usually contain an email address or a personal name. They are less common for general internet use than usernames and passwords. However, they are often used in VPNs to identify devices.
Securing Emails (Email Certificates)
Email certificates help make sure your emails are safe. They can prove that an email hasn't been changed and can also encrypt messages. To send encrypted emails, both people need to have each other's digital certificates. This way, they can trust that their messages are private.
Special Certificates: Root and Self-Signed
A self-signed certificate is a special kind of certificate. It's like a digital ID card that you sign yourself. This means the owner and the signer are the same. These are useful in specific situations, like when your computer encrypts your own files.
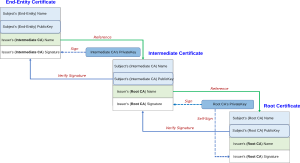
The very first certificate in a chain of trust is a self-signed certificate called a root certificate. A certificate authority signs its own root certificate. This allows the CA to then sign many other certificates.
An intermediate certificate is used to sign other certificates, just like a root certificate. But an intermediate certificate is not self-signed. It must be signed by a root certificate or another intermediate certificate.
An end-entity certificate (or leaf certificate) is any certificate that cannot sign other certificates. Most certificates you encounter, like those for websites or emails, are end-entity certificates.
Other Types of Certificates
- EMV certificate: Used in payment cards (like credit cards) to make sure the card is real during a transaction.
- Code-signing certificate: Helps check if computer programs or apps are real and haven't been changed by someone else.
- Qualified certificate: A special certificate, mostly used in Europe, for digital signatures that have the same legal power as a handwritten signature.
What Information is in a Certificate?
Digital certificates contain important details that help them work. Here are some common pieces of information you might find:
- Serial Number: A unique number for the certificate from the issuer.
- Subject: The person, computer, or organization the certificate belongs to.
- Issuer: The company or entity that checked the information and signed the certificate.
- Not Before: The date and time when the certificate becomes valid.
- Not After: The date and time when the certificate stops being valid.
- Key Usage: What the certificate's public key can be used for (e.g., signing things, encrypting data).
- Extended Key Usage: Specific applications where the certificate can be used (e.g., securing websites, protecting emails).
- Public Key: The public key that belongs to the certificate's subject.
- Signature Algorithm: The method used to create the digital signature.
- Signature: The digital signature itself, made using the issuer's private key.
Who Issues Certificates?
In the world of digital certificates, a certificate authority (CA) is in charge of signing certificates. Think of a CA as a trusted third party. They process requests from people or organizations who want certificates. They check the information and then sign the certificate if everything is correct.
To do this job, a CA needs to have one or more widely trusted root certificates. These root certificates are often built into popular software like web browsers. This makes it easy for your computer to trust certificates issued by that CA. CAs also keep track of which certificates have been canceled (revoked). They share this information using services like Online Certificate Status Protocol (OCSP). Some big certificate authorities include IdenTrust, DigiCert, and Sectigo.
Root Programs: Who Do Computers Trust?
Many major software programs, like web browsers, have a built-in list of certificate authorities they trust. This helps users know that the certificates they see are real. It also helps website owners get certificates that most people's computers will trust. This is very important for HTTPS websites.
The rules and steps a software provider uses to decide which certificate authorities to trust are called root programs. Some of the most important root programs are:
- Microsoft Root Program
- Apple Root Program
- Mozilla Root Program
- Oracle Java root program
- Adobe Approved Trust List (AATL)
Most web browsers (except Firefox) use the trusted list from your computer's operating system. For example, Chrome on Windows uses the Microsoft Root Program's list. Firefox uses its own Mozilla Root Program list on all types of computers. The Mozilla Root Program is open to the public. Because of this, its list of trusted certificates is used by many other open-source programs and Linux systems.
Root programs also say what each trusted certificate authority can be used for. For example, some CAs might be trusted for website certificates but not for signing computer code.
What Happens if a Certificate is Canceled?
Sometimes, a certificate needs to be canceled (or revoked) before its normal expiry date. This happens if the key is stolen, or if there was a mistake when the certificate was issued. Without revocation, a bad person could keep using a stolen certificate. So, canceling certificates is a very important part of keeping things secure. The certificate authority that issued the certificate is responsible for revoking it.
When a certificate is revoked, the CA sends out a message saying it's no longer valid. Your computer needs to check this information. However, checking every certificate all the time can slow things down and use a lot of internet data. Because of this, web browsers sometimes limit how often they check for revoked certificates. This means there's a small chance a bad certificate could be used for a short time before it's fully blocked.
How Certificates Make Websites Secure
The most common use for certificates is with HTTPS websites. When you visit a secure website, your web browser checks the website's certificate. This helps you know that the website is real and that no one is secretly listening to your conversation. This security is vital for things like online shopping.
Here's how it generally works: A website owner asks a certificate authority for a certificate. They send a special electronic document called a certificate signing request. This request includes the website's name, company details, and its public key. The certificate authority then signs this request, creating the public certificate.
When you visit the website, this public certificate is sent to your web browser. It proves that the certificate authority believes the website owner is who they say they are. This helps ensure that you are connecting to the correct website.
Certificate providers can issue different types of certificates, depending on how much checking they do:
- Domain Validation (DV): The easiest to get. The provider only checks if the person asking for the certificate controls the website's domain name.
- Organization Validation (OV): The provider checks if the person controls the domain name and if their organization is a real legal entity.
- Extended Validation (EV): This is the strictest. The provider manually checks the legal identity of the organization. Until recently, browsers showed a green bar with the company name for EV certificates, but this visual cue is now less common.
What are the Weaknesses?
Even though certificates make websites much safer, there are some things to know.
- Your web browser might not warn you if a website suddenly uses a different certificate.
- Governments might be able to order certificate providers to create certificates for certain purposes, like law enforcement.
- All web browsers come with a long list of trusted root certificates. These are controlled by many different organizations. Each of these organizations can issue certificates for any website. This means you rely on the browser developer to manage this list and on the certificate providers to act responsibly.
- Sometimes, fake certificates have been issued. While browsers often catch these, it can take time.
- You can also add new root certificates to your browser. If someone gains access to your computer, they could install a new root certificate. Then, your browser would trust websites using that inserted certificate, even if they are not legitimate.
Why Certificates are Still Important
Despite these weaknesses, using certificates with TLS is considered a must for any website that handles private information or money. This is because, in practice, websites secured with public key certificates are still much, much safer than websites that don't use them (regular "http://" websites).
|
 | Georgia Louise Harris Brown |
 | Julian Abele |
 | Norma Merrick Sklarek |
 | William Sidney Pittman |