Stream cipher facts for kids
A stream cipher is a special type of secret code used in cryptography. Imagine you have a secret message, like "HELLO". A stream cipher encrypts this message one tiny piece at a time, usually one bit or byte. It's like having a very long, random-looking secret key that changes for each piece of your message.
This secret key is called a keystream. It's not truly random, but it looks random enough to keep your message safe. The stream cipher combines your message with this keystream using a special math trick called an exclusive-or (XOR) operation. This makes your message look like gibberish to anyone who doesn't have the secret key.
Stream ciphers are different from block ciphers. Block ciphers encrypt large chunks of data all at once. Stream ciphers are often faster and need less computer power. However, they can be risky if not used correctly. For example, you should never use the same starting point (called the "state") twice to encrypt different messages.
A stream cipher uses a small, secret key, like a 128-bit key. From this key, it creates the long, random-looking keystream. This is similar to how a one-time pad works, but because the keystream isn't truly random, stream ciphers aren't as perfectly secure as a one-time pad. Still, they are very strong when designed well.
Contents
How Stream Ciphers Work
A stream cipher creates its secret keystream based on its internal "state," which you can think of as its current secret settings. This state changes as the cipher works.
There are two main ways the state can change:
- Synchronous stream ciphers: The secret settings change on their own, without caring about the message being encrypted or decrypted.
- Self-synchronizing stream ciphers: The secret settings update based on parts of the message that have already been encrypted.
Synchronous Stream Ciphers
In a synchronous stream cipher, a stream of random-looking numbers is created. This stream is completely separate from your actual message. Then, this random stream is mixed with your message (to encrypt it) or with the encrypted message (to decrypt it) using the XOR operation. When we use single bits and XOR, it's called a binary additive stream cipher.
For this type of cipher to work, both the sender and receiver must be perfectly in sync. If even one bit is added or removed from the message during sending, the receiver will get out of sync. This means the rest of the message will be decrypted incorrectly. To fix this, you might have to try different starting points until the message makes sense again.
If a bit just gets changed (corrupted) during sending, only that single bit in the message will be wrong. The error won't spread to other parts of the message. This can be good if there are many errors during transmission. However, it also means that if an attacker can change a bit in the encrypted message, they can make a predictable change to the original message. For example, if they flip a bit in the encrypted text, the same bit will flip in the decrypted text.
Self-Synchronizing Stream Ciphers
Self-synchronizing stream ciphers are different. They use a part of the previously encrypted message to create the next part of the keystream. These are also called asynchronous stream ciphers.
The cool thing about self-synchronizing ciphers is that the receiver will automatically get back in sync after receiving a few encrypted bits. This makes it easier to recover if some bits are lost or added during transmission. If a single bit is corrupted, it only affects a few bits of the original message, not the whole thing. It's also harder for attackers to make predictable changes to the message with these ciphers compared to synchronous ones.
An example of a self-synchronizing stream cipher is a block cipher used in a special way called "cipher-feedback mode" (CFB).
Building Stream Ciphers
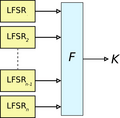
Many binary stream ciphers are built using something called linear feedback shift registers (LFSRs). These are easy to make in computer hardware and can be analyzed mathematically. However, using only LFSRs isn't enough to make a cipher truly secure. So, designers use different tricks to make them stronger.
Using Non-Linear Functions
LFSRs are "linear," which means they follow a simple, predictable pattern. To make them less predictable, designers take the outputs from several LFSRs and feed them into a "non-linear" Boolean function. This creates a more complex and secure keystream.
Clock-Controlled Generators
Normally, LFSRs produce bits at a steady pace. Another trick is to make them produce bits irregularly. This is controlled by the output of a second LFSR. Examples include the stop-and-go generator and the shrinking generator.
The stop-and-go generator uses two LFSRs. One LFSR only moves forward if the second LFSR outputs a "1." If the second LFSR outputs a "0," the first one stays put. The output is then sometimes combined with a third LFSR.
The shrinking generator uses two LFSRs that both move regularly. If the first LFSR outputs a "1," the output of the second LFSR is used as part of the keystream. But if the first LFSR outputs a "0," the output of the second LFSR is thrown away, and no bit is added to the keystream at that moment.
Security of Stream Ciphers
For a stream cipher to be secure, the keystream it produces must be very, very long before it starts repeating itself. If the keystream repeats too soon, attackers can find patterns and potentially figure out your secret message. There are special methods that can be used to break ciphers if the keystream repeats.
Where Stream Ciphers Are Used
Stream ciphers are often used when messages come in pieces of different, unknown lengths. This happens a lot in secure wireless connections. If you used a block cipher in these situations, you'd often have to add extra "padding" to make the message fit into fixed-size blocks, which wastes data. Stream ciphers avoid this by working on the smallest pieces of data, usually bytes.
Another cool use for stream ciphers is in military cryptography. The super-secret keystream can be made by a highly secure encryption machine. Then, this keystream can be fed to other devices, like a radio, which just do the simple XOR operation. This means the radio itself doesn't need to be as super-secure, making it easier to use in different environments.
RC4 is a very popular stream cipher used in software. Other well-known stream ciphers include:
- A5/1
- A5/2
- Helix
- ISAAC
- Phelix
- Salsa20
- SEAL
- SOBER-128
- Trivium
- WAKE
Images for kids
-
The operation of the keystream generator in A5/1, a LFSR-based stream cipher used to encrypt mobile phone conversations.
-
Lorenz SZ cipher machine as used by the German military during World War II
See also
 In Spanish: Cifrador de flujo para niños
In Spanish: Cifrador de flujo para niños
 | Kyle Baker |
 | Joseph Yoakum |
 | Laura Wheeler Waring |
 | Henry Ossawa Tanner |