Blowfish (cipher) facts for kids
Blowfish is a special computer code used to keep information secret. It was created in 1993 by a smart person named Bruce Schneier. Think of it like a secret language that only you and your friend know. Blowfish helps protect your messages and data from others who shouldn't see them. It's known for being fast when it encrypts (scrambles) information.
Contents
What is Blowfish?
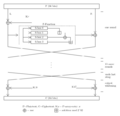
Blowfish is a type of cryptography called a symmetric block cipher. This means it uses the same secret key to both scramble and unscramble data. It works by taking small chunks (called "blocks") of information, 64 bits at a time, and mixing them up using the secret key. Since 1993, many computer programs have used Blowfish to keep data safe.
Why Blowfish Was Made
Bruce Schneier made Blowfish to replace older encryption methods like the DES algorithm. He also wanted to fix problems found in other secret codes. When Blowfish was first released, many other encryption methods were secret or cost money to use.
Schneier wanted Blowfish to be different. He said that Blowfish is not patented, meaning no one owns it. Anyone can use it for free. This made it very popular for many uses.
How Blowfish Works
Blowfish uses a special design that makes it strong and fast.
- It has something called key-dependent S-boxes. These are like secret lookup tables that change based on the secret key you use. This makes it harder for someone to guess how it works.
- It also has a very complex key schedule. This is the process that prepares the secret key for use.
Speed and Keys
Blowfish is one of the fastest block ciphers for encrypting data. However, it takes a bit of time to set up a new secret key. This setup time is about the same as encrypting 4 kilobytes of text. This might be slow for tiny devices like early smartcards. But for most computer programs, it's not a problem.
In fact, this slow key setup can be a good thing! For example, the OpenBSD operating system uses a method similar to Blowfish for protecting passwords. The extra time it takes to set up the key makes it much harder for attackers to guess passwords using a "dictionary attack" (trying many common words).
How Secure is Blowfish?
Blowfish uses a 64-bit block size. This means it scrambles information in chunks of 64 bits. It can also use secret keys of different lengths, from 0 bits up to 448 bits.
It uses a process called a Feistel cipher with 16 rounds. Think of "rounds" as steps in the scrambling process. More rounds generally mean more security.
Known Attacks
In 1996, a researcher named Serge Vaudenay found a way to break a simplified version of Blowfish. This attack needed to know some of the original (unscrambled) text. He also found some "weak keys" that could be broken more easily. However, these attacks do not work against the full 16-round version of Blowfish that people use.
Another researcher, Vincent Rijmen, found a way to break four rounds of Blowfish using a different type of attack. But even this attack could not break the full 16 rounds.
As of 2008, there was no known way to break the full 16-round Blowfish without simply trying every possible key (a "brute-force search"). However, in 2007, Bruce Schneier suggested using a newer algorithm called Twofish instead. While Blowfish is still used, Twofish is considered even more secure for today's needs.
Related pages
- Advanced Encryption Standard
- eSTREAM - A project that looked at new stream ciphers.
- Twofish
- MacGuffin
Images for kids
See also
 In Spanish: Blowfish para niños
In Spanish: Blowfish para niños
 | Sharif Bey |
 | Hale Woodruff |
 | Richmond Barthé |
 | Purvis Young |