OpenBSD facts for kids

Free, Functional, and Secure
|
|
|
|
| Company / developer | Theo de Raadt et al. |
|---|---|
| Programmed in | C, assembly, Perl, Unix shell |
| OS family | Unix-like (BSD) |
| Working state | Current |
| Source model | Open source |
| Initial release | July 1996 |
| Package manager | OpenBSD package tools |
| Supported platforms | Alpha, x86-64, ARMv7, ARMv8 (64-bit), PA-RISC, IA-32, LANDISK, Loongson, Omron LUNA-88K, MIPS64, macppc, PowerPC, 64-bit RISC-V, SPARC64 |
| Kernel type | Monolithic |
| Userland | BSD |
| Default user interface | Modified pdksh, X11 (FVWM) |
| License | BSD, ISC, other permissive licenses |
OpenBSD is a special kind of operating system that helps computers run. It's like the brain of a computer. OpenBSD is known for being very focused on security, which means it's designed to be super safe from hackers and bad software. It's also free software, so anyone can use, change, and share it.
OpenBSD is based on something called Berkeley Software Distribution (BSD), which is a type of Unix-like system. A person named Theo de Raadt started OpenBSD in 1995. He wanted to create a system that was easy to move to different computers, followed rules for how software should work, fixed problems quickly, and had strong security built-in.
Many parts of OpenBSD are used in other computer systems. For example, the firewall (a security guard for your computer's network) in Apple's macOS uses code from OpenBSD. Also, parts of Android and even Windows 10 use OpenBSD's OpenSSH (a secure way to connect to other computers).
The word "open" in OpenBSD means that its source code (the instructions that make it work) is available for everyone to see and use on the Internet. It also means that OpenBSD can run on many different types of computers and devices.
Contents
History of OpenBSD
In 1994, Theo de Raadt left another project called NetBSD because of disagreements. In October 1995, he started OpenBSD. The first official version, OpenBSD 2.0, came out in October 1996. Since then, a new version of OpenBSD has been released every six months. Each version is supported for one year.
In 2007, the OpenBSD Foundation was created. This is a non-profit group that helps support OpenBSD and related projects. By 2024, OpenBSD had changed so much that almost none of its original code from NetBSD remained.
How Many People Use OpenBSD?
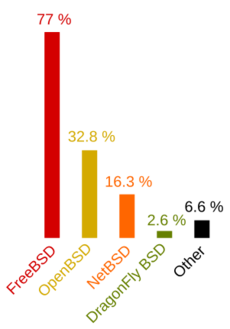
It's hard to know exactly how many people use OpenBSD because its creators don't track this information.
In 2005, a survey found that about 32.8% of BSD users used OpenBSD. This was less than FreeBSD (77%) but more than NetBSD (16.3%). However, the people who did the survey said it might not be completely accurate because it mostly reached people who were already part of the BSD community.
What Can OpenBSD Be Used For?
Network Devices
OpenBSD is great for making routers or wireless hotspots because it has strong networking features. Its security tools, like its built-in cryptography and packet filter, make it perfect for things like firewalls and VPN connections.
Some companies even use OpenBSD to build their own security devices.
Other Operating Systems
Parts of OpenBSD's code are used in other operating systems. For example, some versions of Microsoft's Windows Services for UNIX use OpenBSD code. The PF firewall from OpenBSD is also used in FreeBSD and macOS.
Personal Computers
OpenBSD comes with a system called Xenocara for its graphical interface, which is like the desktop you see on your computer. This makes it suitable for use on personal computers, including laptops.
As of September 2018, OpenBSD had about 8000 software packages available. These include popular desktop environments like GNOME and KDE Plasma, and web browsers like Firefox and Chromium.
Servers
OpenBSD can also be set up as a server for many different tasks. It can be a mail server, a web server, an FTP server (for sharing files), a DNS server (for finding websites), or a router. Since version 6.8, OpenBSD has also included WireGuard support, which is a modern way to create secure network connections.
Security Focus
Soon after OpenBSD started, its creator, Theo de Raadt, worked with a security company. This partnership helped make security the main goal of the OpenBSD project.
OpenBSD has many features designed to make it more secure:
- It uses safer ways to handle common programming tasks.
- It changes how programs are built to help find and prevent security problems.
- It uses special memory protection to stop bad programs from accessing parts of the computer they shouldn't.
- It uses strong cryptography (secret codes) and randomization (making things unpredictable) to make it harder for attackers.
- It limits what programs can do, like what files they can access.
To make it even safer, many programs in OpenBSD are designed to use "privilege separation." This means a program is split into parts, and only the necessary part gets special permissions. Once it's done with those permissions, it drops them. This is like a security guard only having keys to the rooms they need to enter, and then giving them back.
OpenBSD developers also created OpenSSH, which is a very popular and secure way to connect to other computers over a network. It's used on many operating systems today.
The project constantly checks its own code for problems. If a bug is found, they don't just fix it; they look for similar issues everywhere else and try to improve their tools to prevent such bugs in the future.
OpenBSD's Security Record
OpenBSD is famous for its security record. For a long time, their website proudly stated:
Five years without a remote hole in the default install!
A "remote hole" means a security flaw that someone could use to break into the system from another computer.
In 2002, a bug was found in OpenSSH that allowed remote access to the main administrator account. This was a big deal, so the slogan changed to:
One remote hole in the default install, in nearly 6 years!
Then, in 2007, another remote security flaw was found. The slogan changed again to:
Only two remote holes in the default install, in a heck of a long time!
This statement refers to the basic, default installation of OpenBSD, which has very few services running. The idea is that if you only run what you need, your system is much safer. OpenBSD encourages users to manually enable any extra services, making them think about security first.
Alleged Backdoor
In 2010, someone claimed that the FBI had paid some former OpenBSD developers to put secret "backdoors" into the system's encryption code years earlier. Theo de Raadt made this claim public and asked all developers to check the code. They fixed some bugs, but they didn't find any evidence of backdoors. De Raadt believed that if backdoors were written, they probably didn't make it into OpenBSD's main code.
Criticisms
Even though OpenBSD is known for security, some experts have pointed out that bugs can still be found in its core system. In 2017, an expert said that while OpenBSD was the best among BSD systems for security, "Bugs are still easy to find." In 2019, another critic claimed that many of OpenBSD's security features were not as effective as believed.
Projects Started by OpenBSD
Many other open-source projects began as parts of OpenBSD, including:
- CARP: A free way to make network connections more reliable.
- cwm: A simple window manager for the desktop.
- doas: A safer tool for running commands with special permissions, similar to sudo.
- OpenBSD httpd: A web server.
- LibreSSL: A secure way to handle internet connections, like when you visit a website with "https."
- OpenBGPD: A program for managing how internet traffic is routed.
- OpenNTPD: A simpler way to keep computer clocks accurate.
- OpenSMTPD: A program for sending and receiving emails.
- OpenSSH: The very popular secure way to connect to other computers.
- PF: A powerful firewall.
Many of these projects are now used in other operating systems too. OpenBSD makes sure its main programs run in a very secure way, limiting what they can do.
How OpenBSD is Developed
OpenBSD is constantly being improved by its team of developers. Anyone with the right skills can help, and the main coordinator is Theo de Raadt. New official versions are released twice a year, and they are supported for 12 months.
Developers often meet at special events called hackathons, where they focus on writing code together. Most new releases of OpenBSD also come with a fun song!
Open Source and Open Documentation
OpenBSD is famous for having great documentation (guides and manuals).
When OpenBSD was created, Theo de Raadt decided that everyone should be able to see its source code. This was a new idea at the time. This decision helped more people get involved and showed OpenBSD's commitment to being open.
OpenBSD does not include any secret, "closed source" software. They believe that if they can't see the code, they can't trust it or fix it if it breaks.
Because OpenBSD is based in Canada, it doesn't have to follow strict US rules about sharing encryption technology. This means it can use the best and strongest encryption methods. For example, it encrypts parts of your computer's memory to keep sensitive data safe.
OpenBSD also makes many parts of the system behave randomly. This makes it harder for attackers to predict how the system will work and find weaknesses.
Licensing
OpenBSD has strict rules about software licenses. It prefers licenses like the ISC license and other BSD licenses, which allow people to use and share the code with very few restrictions. They avoid licenses like the GNU General Public License because they consider them too restrictive.
In 2001, OpenBSD checked all its code to make sure every part followed the correct license rules. They removed or replaced any code that didn't meet their standards. For example, they created their own PF firewall because the original firewall they used had new, unacceptable license rules.
Funding OpenBSD
Even though parts of OpenBSD are used in commercial products, most of its money comes from donations from individual users and from people buying their CD-ROM sets.
In the early 2000s, OpenBSD received some funding from a US government agency called DARPA, which helped pay developers' salaries and for equipment.
In 2006, OpenBSD faced financial difficulties. Companies like the Mozilla Foundation and GoDaddy helped them out. However, Theo de Raadt noted that most of the support came from individual users, not big companies.
In 2014, OpenBSD needed money for electricity bills and faced shutting down. They received a large donation in bitcoins and raised enough money to secure their future for a while.
OpenBSD Foundation
| Formation | July 25, 2007 |
|---|---|
| Founder | OpenBSD developers |
| Legal status | Nonprofit organization |
| Location |
The OpenBSD Foundation is a non-profit group in Canada. It was started in 2007 to be the main contact point for people and organizations who want to support OpenBSD. It also helps protect other projects connected to OpenBSD, like OpenSSH and LibreSSL.
Since 2014, big companies like Microsoft, Facebook, and Google have given money to the OpenBSD Foundation. In 2015, Microsoft became a "gold level" supporter, donating a lot of money to help develop OpenSSH, which Microsoft had started using in its own products.
How to Get OpenBSD
OpenBSD is free to get in several ways. You can download its code or ready-to-use versions from the internet. In the past, you could order CD-ROM sets with cool artwork and a theme song, which helped fund the project. However, they stopped releasing CD-ROM sets after version 6.0.
OpenBSD has a system called pkg* tools to easily install and manage extra programs that aren't part of the main system. These programs are built to work perfectly with each specific version of OpenBSD.
Songs and Artwork
At first, OpenBSD used a version of the BSD daemon as its mascot. But later, they chose a pufferfish named Puffy. Since then, Puffy has been on OpenBSD's promotional items and in its release songs and artwork.
Each OpenBSD release often has a unique theme, with special artwork, posters, and T-shirts. They also create a theme song for each release, which often uses humor or parody to share a message important to the project.
For example, OpenBSD 3.3 had Puff the Barbarian, a rock song parodying Conan the Barbarian that talked about open documentation. OpenBSD 3.7 featured The Wizard of OS, a song styled after Pink Floyd and parodying The Wizard of Oz, which was about wireless technology. OpenBSD 3.8 had Hackers of the Lost RAID, a parody of Indiana Jones that highlighted new data storage tools.
OpenBSD Versions Over Time
OpenBSD releases a new version every six months. Here's a summary of some of the important changes over the years:
| Version | Release date | Supported until | What's New |
|---|---|---|---|
| 2.0 | 1 October 1996 | This was the first official release of OpenBSD. | |
| 2.6 | 1 December 1999 | The first release of OpenSSH, which is now used everywhere for secure connections. | |
| 3.0 | 1 December 2001 | The pf packet filter (firewall) was created and included. | |
| 3.1 | 19 May 2002 | The first official remote security flaw was found in OpenSSH. | |
| 3.3 | 1 May 2003 | Introduced the W^X feature, which makes memory safer by preventing programs from writing and running code in the same place. | |
| 3.4 | 1 November 2003 | Started using Address space layout randomization (ASLR) by default, which makes it harder for attackers to predict where things are in memory. | |
| 3.5 | 1 May 2004 | Introduced CARP, a free alternative for making networks more reliable. | |
| 3.8 | 1 November 2005 | 1 November 2006 | The telnet program, which was not secure, was completely removed. |
| 4.0 | 1 November 2006 | 1 November 2007 | A second official remote security flaw was found. |
| 4.6 | 18 October 2009 | 1 November 2010 | Introduced smtpd(8), a new secure email server, and tmux(1), a tool for managing multiple terminal windows. |
| 5.3 | 1 May 2013 | 1 May 2014 | Started using Position-independent executables (PIE) by default, which improves security. |
| 5.5 | 1 May 2014 | 1 May 2015 | Introduced signify(1) for checking cryptographic signatures of releases and packages. Also, it became ready for the Year 2038 problem on all platforms. |
| 5.6 | 1 November 2014 | 18 October 2015 | LibreSSL, a new version of OpenSSL, was created and included. |
| 5.8 | 18 October 2015 | 1 September 2016 | This was the 20th anniversary release. It included doas(1), a replacement for sudo. |
| 5.9 | 29 March 2016 | 11 April 2017 | The W^X security feature was fully enforced in the main system. |
| 6.0 | 1 September 2016 | 9 October 2017 | Removed support for older computer architectures like vax and 32-bit SPARC. |
| 6.1 | 11 April 2017 | 15 April 2018 | Introduced syspatch(8) for easier system updates. Added support for the new arm64 platform. |
| 6.2 | 9 October 2017 | 18 October 2018 | Clang became the default compiler for i386 and amd64 computers. |
| 6.3 | 2 April 2018 | 3 May 2019 | Improved support for multiple processors on arm64. Included fixes for security issues like Meltdown/Spectre. |
| 6.4 | 18 October 2018 | 17 October 2019 | Introduced unveil(2), a new way to limit what parts of the file system programs can see. |
| 6.5 | 24 April 2019 | 19 May 2020 | The Xorg (X Window Server) was made more secure. |
| 6.6 | 17 October 2019 | 18 October 2020 | Introduced sysupgrade(8) to automate upgrades to new releases. |
| 6.7 | 19 May 2020 | 1 May 2021 | Made ffs2 the default file system type for most installations. |
| 6.8 | 18 October 2020 | 14 October 2021 | This was the 25th anniversary release. |
| 6.9 | 1 May 2021 | 21 April 2022 | This was the 50th release of OpenBSD. |
| 7.0 | 14 October 2021 | 20 October 2022 | Introduced support for the new riscv64 platform. |
| 7.1 | 21 April 2022 | 10 April 2023 | This was the 52nd release. |
| 7.2 | 20 October 2022 | 16 October 2023 | This was the 53rd release. |
| 7.3 | 10 April 2023 | 5 April 2024 | Added support for full-disk encryption during installation. |
| 7.4 | 16 October 2023 | 8 October 2024 | This was the 55th release. |
| 7.5 | 5 April 2024 | 28 April 2025 | This was the 56th release. |
See also
 In Spanish: OpenBSD para niños
In Spanish: OpenBSD para niños
- Comparison of BSD operating systems
- OpenBSD security features
- Security-focused operating system
 | Madam C. J. Walker |
 | Janet Emerson Bashen |
 | Annie Turnbo Malone |
 | Maggie L. Walker |