Key schedule facts for kids
In cryptography, the science of making and breaking secret codes, some secret codes work in many "rounds" or steps. Each step uses a small part of the main secret key, called a subkey. A key schedule is like a recipe. It's a set of instructions that takes the main secret key and figures out all the smaller subkeys needed for each step of the coding process. This makes sure the secret code is strong and hard to crack.
How Key Schedules Work
Different secret codes use different ways to create their key schedules. Some are very simple, while others are quite complex. The goal is always to make the code as secure as possible.
Simple Key Schedules
Some secret codes have very straightforward key schedules. For example, a code called TEA uses a 128-bit key. This key is simply split into four smaller 32-bit pieces. These pieces are then used over and over again in the different steps of the coding process.
Complex Key Schedules
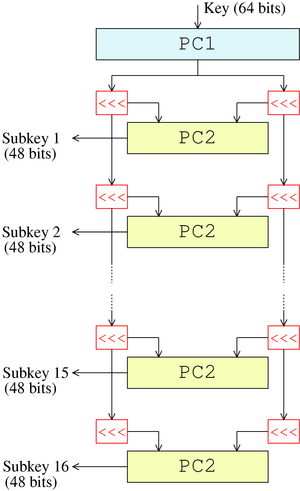
Other codes, like the DES, use more complex key schedules. The DES code uses a 56-bit key. This key is split into two halves, each 28 bits long.
In each step of the DES coding process, both halves of the key are rotated (shifted around) by one or two bits. After this shifting, 48 bits are chosen to form the subkey for that step. These 48 bits are picked from both halves of the main key. Because the key halves keep rotating, a different set of bits is used for almost every subkey. This makes the code stronger.
Many modern secret codes use even more complicated key schedules. They do this to protect against special attacks where code breakers try to find patterns between the main key and the subkeys. These complex schedules often use a special mathematical rule that's easy to do one way but very hard to undo. This rule helps create a much larger "expanded key" from which the subkeys are then taken.
Some codes, like AES (which is used for many secure things today) and Blowfish, even use parts of their own coding process to create their key schedules. They sometimes start with special numbers that are chosen carefully to make the process even more secure. Other codes, like RC5, use completely different rules to expand their keys compared to their main coding functions.
Experts have found that a well-designed key schedule is very important for making secret codes strong. It helps make it harder for code breakers to guess the secret key using special mathematical tricks.
Images for kids
 | John T. Biggers |
 | Thomas Blackshear |
 | Mark Bradford |
 | Beverly Buchanan |