Tiny Encryption Algorithm facts for kids
|
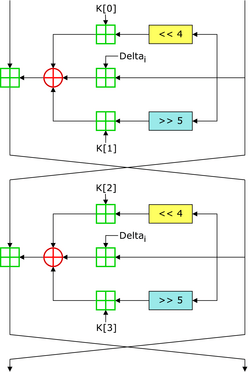
Two Feistel rounds (one cycle) of TEA
|
|
| General | |
|---|---|
| Designers | Roger Needham, David Wheeler |
| First published | 1994 |
| Successors | XTEA |
| Cipher detail | |
| Key sizes | 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel network |
| Rounds | variable; recommended 64 Feistel rounds (32 cycles) |
| Best public cryptanalysis | |
| TEA suffers from equivalent keys (see text; Kelsey et al., 1996) and can be broken using a related-key attack requiring 223 chosen plaintexts and a time complexity of 232. The best structural cryptanalysis of TEA in the standard single secret key setting is the zero-correlation cryptanalysis breaking 21 rounds in 2121.5 time with less than the full code book | |
In cryptography, the Tiny Encryption Algorithm (TEA) is a special way to scramble information so that only certain people can read it. It's like a secret code! It was created by two smart people, David Wheeler and Roger Needham, at Cambridge Computer Laboratory in 1994. TEA is famous because it's very simple to understand and use, often needing just a few lines of computer code. It's also free for anyone to use, without needing to pay for patents.
How TEA Works
TEA takes a small piece of information, like a 64-bit block of data, and scrambles it using a 128-bit key. Think of the key as the secret password that locks and unlocks the information.
It uses a special method called a Feistel network. This method mixes up the data many times. For TEA, it's suggested to do this 64 times, which are often grouped into pairs called cycles.
To make sure the scrambling is strong, TEA uses a special "magic number" (0x9E3779B9). This number helps prevent simple ways of breaking the code. It makes sure each step of the scrambling is unique.
Why TEA Was Improved
Even though TEA is simple, it has a few weaknesses. One big problem is that some different keys can actually do the same thing. This means the secret key isn't as unique as it should be. It's like having four different passwords that all open the same lock.
Because of this, TEA wasn't very good for making hash functions. A hash function creates a unique digital fingerprint for data. This weakness was even found when people looked at how the Xbox game console used TEA for certain tasks.
TEA also had another weakness: a related-key attack. This is a special way for someone to try and figure out the key if they can get the system to encrypt certain messages for them.
Because of these issues, a new and improved version called XTEA was created to fix these problems.
Different Versions of TEA
Over time, the creators made improvements to TEA:
- Block TEA: This was an updated version that could scramble larger pieces of information, not just the small 64-bit blocks of the original TEA. It was released along with XTEA.
- XXTEA: Published in 1998, this was a third version. It brought even more improvements to make the Block TEA algorithm more secure and harder to break.
See also
 | Kyle Baker |
 | Joseph Yoakum |
 | Laura Wheeler Waring |
 | Henry Ossawa Tanner |