XTEA facts for kids
|
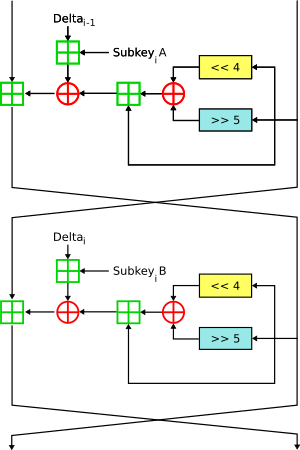
Two Feistel rounds (one cycle) of XTEA
|
|
| General | |
|---|---|
| Designers | Roger Needham, David Wheeler |
| First published | 1997 |
| Derived from | TEA |
| Successors | Corrected Block TEA |
| Cipher detail | |
| Key sizes | 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel cipher |
| Rounds | variable; recommended 64 Feistel rounds (32 cycles) |
| Best public cryptanalysis | |
| A related-key rectangle attack on 36 rounds of XTEA (Lu, 2009) | |
In the world of cryptography, which is about secret codes, XTEA (short for eXtended TEA) is a special type of code. It's called a block cipher. XTEA was created to fix some problems found in an older code called TEA.
Two smart people, David Wheeler and Roger Needham, designed XTEA. They worked at the University of Cambridge Computer Laboratory in England. They shared their new code in a report in 1997. Good news: no one owns a patent on XTEA, so anyone can use it!
Like TEA, XTEA works with blocks of information. It takes 64 bits of data at a time. It uses a secret key that is 128 bits long. XTEA is a Feistel cipher, which is a specific way of mixing up data. It usually goes through 64 "rounds" to make the data super secure. XTEA is a bit more complex than TEA. It mixes up the key and data in different ways.
Contents
What is XTEA?
XTEA is a way to scramble information so that only someone with the secret key can read it. Think of it like a very complex lock and key for digital messages. It's used to keep data safe and private. This type of code is important for things like online shopping or sending secret messages.
How XTEA Works
XTEA takes a small chunk of data, called a "block," and turns it into a secret code. It does this by using a secret "key." The key is like a password that tells the code how to scramble and unscramble the data.
The process involves many steps, called "rounds." In each round, the data is mixed and changed using the key. This makes it very hard for anyone without the key to figure out the original message. XTEA uses a structure called a Feistel cipher. This structure helps to make the coding process strong and reversible. Reversible means you can easily undo the scrambling if you have the key.
Why XTEA Was Made
XTEA was created because the older TEA code had some weaknesses. These weaknesses meant that very smart people could sometimes find ways to break the code. XTEA was designed to be stronger and more secure. It uses a slightly different way of mixing the key and data. This makes it harder for code-breakers to find patterns and unlock the secret message.
Using XTEA in Programs
XTEA can be written in many computer languages. For example, it can be written in C. Programmers use this code to make sure information is kept secret. They can use it to encrypt (scramble) data and then decrypt (unscramble) it later. This is useful for protecting files or messages.
Finding Weaknesses in XTEA
Even strong codes like XTEA are studied by experts. This study is called cryptanalysis. These experts try to find any weaknesses or shortcuts to break the code without the key. It's like trying to pick a lock without having the right key.
Over the years, people have found some ways to attack XTEA. For example, in 2004, some researchers found a way to attack 27 out of 64 rounds of XTEA. In 2009, another person found a way to attack 36 rounds. These attacks usually need a lot of information and computer power. But finding these weaknesses helps make future codes even stronger. It's a bit like a puzzle where people keep trying to find new ways to solve it.
Block TEA
Along with XTEA, another code called Block TEA was also introduced. Block TEA uses the same basic scrambling steps as XTEA. However, Block TEA works on an entire message at once, not just small blocks. This means it doesn't need extra rules for how to handle different parts of a message.
Block TEA also had some weaknesses. These weaknesses were found and studied by experts. These studies helped lead to an even newer and stronger code called XXTEA.
See also
 | Emma Amos |
 | Edward Mitchell Bannister |
 | Larry D. Alexander |
 | Ernie Barnes |