Feistel cipher facts for kids
In cryptography, which is the study of secure communication, a Feistel cipher is a common design used to create block ciphers. It's named after a German cryptographer named Horst Feistel. You might also hear it called a Feistel network. Many important block ciphers use this design, including the famous Data Encryption Standard (DES).
One great thing about the Feistel design is that the steps for encryption (turning normal text into secret code) and decryption (turning secret code back into normal text) are very similar. Sometimes, they are almost exactly the same! This means that the computer code or electronic parts needed to make the cipher work can be much smaller, saving space and effort.
The Feistel design works in steps, repeating the same process many times. This makes it easier to build these ciphers into computer hardware.
Feistel networks are a type of "product cipher." This means they combine several rounds of simple operations to make the data very scrambled and secure. These operations include:
- Bit-shuffling: This mixes up the bits (the smallest pieces of data) in a specific way. Think of it like shuffling a deck of cards. This helps spread changes throughout the data.
- Substitution: This replaces small groups of bits with other groups of bits using special rules. This makes the relationship between the original data and the scrambled data very complex.
- Mixing with XOR: This uses a mathematical operation called XOR to combine parts of the data with a secret key. This adds to the confusion and mixing of the data.
These steps work together to create "confusion and diffusion". Confusion makes it hard to guess the secret key from the scrambled data. Diffusion makes sure that changing just one bit in the original data changes many bits in the scrambled data.
Contents
How Feistel Ciphers Work
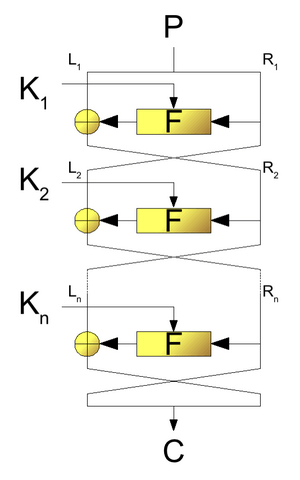
Imagine you have a message you want to encrypt. A Feistel cipher first splits your message (which is a block of data) into two equal halves. Let's call them the left side (L) and the right side (R).
Then, the cipher goes through several "rounds." In each round, it does these steps:
- The right side (R) of the data becomes the new left side for the next step.
- The old left side (L) is combined with a special function of the right side (R) and a secret key for that round. This combination uses the XOR operation. The result becomes the new right side.
This process repeats for many rounds. After all the rounds are done, the two halves are put back together to form the encrypted message, which is called the ciphertext.
The amazing part is that to decrypt the message, you just do the same steps in reverse order, using the secret keys in the opposite order. This is why encryption and decryption are so similar!
One big advantage of this design is that the special function used in each round doesn't have to be reversible. This means it can be very complex and hard to undo, which makes the cipher stronger.
Sometimes, Feistel ciphers are "unbalanced." This means the two halves of the data (L and R) are not equal in length. An experimental cipher called MacGuffin is an example of this.
The Feistel design is also used in other areas of cryptography, not just for block ciphers. For example, it helps make sure that encrypted messages are random and secure in some public-key encryption systems.
Why Feistel Ciphers Are Secure
Many modern block ciphers use the Feistel design because it's very secure. Experts called cryptographers have studied Feistel ciphers a lot to understand how strong they are.
Two important cryptographers, Michael Luby and Charles Rackoff, proved something very important. They showed that if the function used in each round is strong and unpredictable, then even a few rounds of the Feistel design can make the cipher very secure.
They found that just 3 rounds are enough to make the cipher behave like a "pseudorandom permutation." This means it scrambles data so well that it looks completely random. With 4 rounds, it becomes even stronger, making it hard for anyone to figure out the original message, even if they have some special tools. Because of their important work, Feistel ciphers are sometimes called Luby-Rackoff block ciphers.
Examples of Feistel Ciphers
Many well-known ciphers use the Feistel design or a modified version of it:
- Blowfish
- Camellia
- CAST-128
- DES
- FEAL
- ICE
- KASUMI
- LOKI97
- Lucifer
- MARS
- MAGENTA
- MISTY1
- RC5
- TEA
- Triple DES
- Twofish
- XTEA
- GOST 28147-89
Some ciphers use a more general version of the Feistel design:
See also
 In Spanish: Cifrado de Feistel para niños
In Spanish: Cifrado de Feistel para niños
 | William Lucy |
 | Charles Hayes |
 | Cleveland Robinson |