Public-key cryptography facts for kids
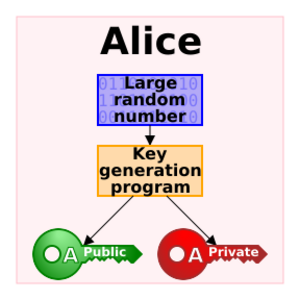
Public-key cryptography, also known as asymmetric cryptography, is a clever way to send secret messages and prove who sent them. Imagine you have two special keys: one you can share with everyone (your public key) and one you must keep totally secret (your private key). These keys are linked by tricky math problems.
The cool thing is, you can share your public key with anyone without making your secrets unsafe. This system is super important for keeping your online messages and data safe. It's used in many internet tools like TLS (which secures websites you visit), SSH (for secure computer connections), and PGP (for secure emails).
Before public-key cryptography, everyone used "symmetric" keys. This meant both the sender and receiver had to use the exact same secret key. Sharing this secret key safely was a big problem, especially if you needed to talk to many different people. Public-key cryptography solved this by letting you share one key openly while keeping the other secret.
Contents
How Public-Key Cryptography Works
There are two main ways public-key cryptography is used:
Digital Signatures
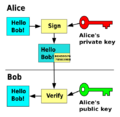
Imagine you want to prove that a message or document really came from you and hasn't been changed. This is where a digital signature comes in.
- You use your private key to create a special "signature" for your message.
- Anyone with your public key can check this signature. They can see that it matches your message and that no one has changed it.
- It's like having a unique stamp only you can make. Everyone can see your stamp and know it's real, but no one else can make a fake one.
For example, a company that makes software can sign their updates with their private key. Your computer uses the company's public key to check the signature. If it matches, your computer knows the update is real and safe to install.
[[File:Private key signing.svg|thumb|In this example the message is digitally signed with Alice's private key, but the message itself is not encrypted.
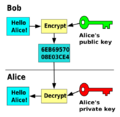
Public-Key Encryption
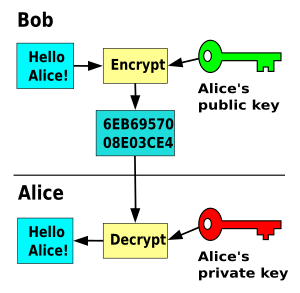
This is about sending secret messages that only the right person can read.
- Anyone who has your public key can use it to encrypt a message for you. This turns the message into a secret code (called ciphertext).
- Only you, with your private key, can decrypt this ciphertext and read the original message.
- It's like having a special mailbox with a public slot where anyone can drop a letter. But only you have the key to open the mailbox and read the letters inside.
For instance, a journalist might put their public key on a website. Sources can then encrypt secret messages using this public key. Only the journalist, who has the private key, can read these messages. Even if someone else intercepts the message, they can't read it without the private key.
However, public-key encryption doesn't hide everything. It doesn't hide who sent the message, when it was sent, or how long it is. It only hides the message content itself.
Making Sure Public Keys Are Real
How do you know that a public key really belongs to the person it claims to? There are a couple of ways:
- A public key infrastructure (PKI) uses trusted organizations called "certificate authorities." These authorities check who owns a key pair and then give them a digital certificate. This certificate is like an ID card for the public key. Websites often use this system.
- A "web of trust" is a more spread-out system. Here, people "vouch" for each other's public keys. It's like your friends introducing you to their friends, and you trust them because your friends do.
How It's Used
Public-key cryptography is used for many important things:
- Keeping secrets: Encrypting messages so only the intended person can read them. This is used in online banking, email, and messaging apps every day.
- Proving who you are: Digital signatures help confirm that a message or document came from a specific person.
- Non-repudiation: This means someone can't deny they sent a message or signed a document. The digital signature proves it.
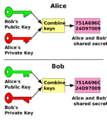
Combining Keys: Hybrid Systems
Public-key cryptography can be slower than symmetric-key cryptography for encrypting large amounts of data. So, many systems use a smart combination called a hybrid cryptosystem.
Here's how it works: 1. Public-key cryptography is used first to securely share a new, secret symmetric key between two parties. 2. Once this symmetric key is shared, both parties use it to encrypt and decrypt all the actual data. Symmetric-key encryption is much faster for this part.
Think of it like this: You use a special, secure public-key "handshake" to secretly agree on a fast, secret code word. Then, you use that fast code word for all your long conversations. This is how things like PGP, SSH, and SSL/TLS work.
[[File:Public key shared secret.svg|thumb| In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key of the pair. After obtaining an authentic (n.b., this is critical) copy of each other's public keys, Alice and Bob can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher.]]
Things to Watch Out For
Like any security system, public-key cryptography has some weak spots:
Keeping Private Keys Secret
The biggest risk is if someone else finds out your private key. If that happens, all your secret messages and digital signatures could be fake or read by others.
Quantum Computers
Scientists are developing super-powerful computers called "quantum computers." These computers could potentially break many of the public-key algorithms we use today. Because of this, new "quantum-resistant" systems are being developed to stay ahead.
Man-in-the-Middle Attacks
Imagine you're trying to exchange public keys with a friend, but a sneaky attacker gets in the middle. This attacker could pretend to be your friend to you, and pretend to be you to your friend. They could swap out your public keys for their own. Then, they could read, change, and re-encrypt all your messages without you knowing.
This kind of attack is harder to do with modern security, but it's a risk if you're using insecure connections, like public Wi-Fi. This is why it's so important to make sure public keys are truly authentic, often through systems like PKI.
Hidden Information (Metadata)
Most public-key encryption only hides the main message. It doesn't hide "metadata" like who sent the message, who received it, when it was sent, or the subject line. This means someone could still learn a lot about who is talking to whom, even if they can't read the messages.
However, new experimental systems are being developed that can also encrypt these header details, making it much harder for outsiders to track communication patterns.
History of Public-Key Cryptography
For a long time, sharing secret keys was a big problem in cryptography. People had to meet in person or send trusted couriers to exchange keys.
Early Ideas
In 1874, a smart person named William Stanley Jevons wrote about how hard it is to find two numbers that multiply to make a very large number. This idea is actually key to how some public-key systems work today.
Secret Discoveries
In the 1970s, some British cryptographers working for the government secretly came up with the idea of "non-secret encryption" (what we now call public-key cryptography). Clifford Cocks developed an algorithm similar to what we now call RSA, and Malcolm J. Williamson developed something like Diffie–Hellman key exchange. These discoveries were kept secret by the government until 1997.
Public Discoveries
In 1976, Whitfield Diffie and Martin Hellman publicly shared a way for two people to agree on a shared secret key over an open channel. This became known as Diffie–Hellman key exchange.
Then, in 1977, three scientists at MIT – Ron Rivest, Adi Shamir, and Leonard Adleman – independently invented an algorithm similar to Cocks's secret discovery. They published their work in 1978, and it became famous as RSA, named after their initials. RSA is still widely used today for both encryption and digital signatures.
Since then, many other public-key methods have been created, making our digital world much safer.
Examples of Public-Key Techniques
Here are some well-known public-key methods:
- Diffie–Hellman key exchange (for securely sharing keys)
- Digital Signature Algorithm (for digital signatures)
- Elliptic-curve cryptography (a more efficient type of public-key crypto)
- RSA (for both encryption and digital signatures)
Examples of Protocols Using Public-Key Algorithms
These are systems that use public-key cryptography to keep things safe:
- S/MIME (for secure email)
- PGP (for secure email and file encryption)
- IPsec (for securing internet communications)
- TLS (secures web browsing, like when you see "https://")
- SSH (for secure remote access to computers)
- Bitcoin (uses digital signatures for transactions)
Images for kids
-
In this example the message is digitally signed with Alice's private key, but the message itself is not encrypted.
-
In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key of the pair. After obtaining an authentic (n.b., this is critical) copy of each other's public keys, Alice and Bob can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher.
See also
 In Spanish: Criptografía asimétrica para niños
In Spanish: Criptografía asimétrica para niños
 | Georgia Louise Harris Brown |
 | Julian Abele |
 | Norma Merrick Sklarek |
 | William Sidney Pittman |