Pretty Good Privacy facts for kids
| Original author(s) |
|
|---|---|
| Developer(s) | Broadcom Inc. |
| Initial release | 1991 |
| Stable release |
11.4.0 Maintenance Pack 2 / May 23, 2023
|
| Written in | C |
| Operating system | macOS, Windows |
| Standard(s) |
|
| Type | Encryption software |
| License | Commercial proprietary software |
Pretty Good Privacy (PGP) is a special computer program that helps keep your digital information private and safe. It uses encryption to scramble messages, emails, files, and even entire computer drives. This makes sure that only the right people can read them. PGP also helps you check if a message really came from the person who sent it, using something called a digital signature.
Phil Zimmermann created PGP in 1991. It quickly became very popular for protecting online communication. PGP and similar programs follow a set of rules called the OpenPGP standard. This means different programs can work together to send and receive encrypted messages.
Some people have pointed out that the OpenPGP standard can be a bit tricky to learn. There was also a security issue called Efail that affected some email programs using OpenPGP. However, new versions and updates are always being made to improve security.
Contents
How PGP Works
PGP uses a clever mix of different methods to keep your data safe. It combines hashing (making a short digital summary), data compression (making files smaller), symmetric-key cryptography (using one secret key for locking and unlocking), and public-key cryptography (using two linked keys, one public and one private).
Each public key in PGP is connected to a username or an email address. The first version of PGP used a "web of trust" system. This was different from other systems that used central authorities to confirm keys. Newer PGP versions also offer automated ways to manage these keys.
Your PGP Fingerprint
A PGP fingerprint is like a short ID for your public key. It's a much shorter version of the long public key. You can use this short fingerprint to check if a public key is the correct one. For example, a fingerprint might look like C3A6 5E46 7B54 77DF 3C4C 9790 4D22 B3CA 5B32 FF66. People can even print these on business cards!
Working with Different PGP Versions
As PGP gets updated, newer versions might have features or ways of encrypting that older PGP systems can't understand. This means that if you encrypt a message with a very new PGP version, someone using a much older version might not be able to open it, even if they have the right key. So, it's a good idea for people using PGP to know what versions their friends or contacts are using.
Keeping Messages Secret
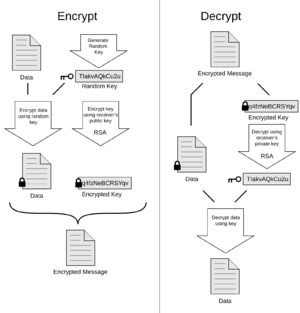
PGP helps you send messages that only the intended person can read. It does this by using a "hybrid" system. First, PGP encrypts your message with a special, one-time secret key called a session key. This session key is only used for that one message. Then, PGP takes this session key and encrypts it using the receiver's public key. Only the receiver's private key can unlock this session key. Once unlocked, the session key can then decrypt the actual message. It's like putting a secret note in a box, then locking the box with a special key, and then putting that special key in another box that only the receiver can open!
Digital Signatures for Trust
PGP can also help you make sure a message is truly from the person who claims to have sent it. This is done with a digital signature. The sender uses PGP to create a unique digital signature for their message. PGP first makes a short summary (a "hash") of the message. Then, it uses the sender's private key to create the digital signature from that summary. The receiver can then use the sender's public key to check if the signature is real and if the message hasn't been changed.
The Web of Trust Explained
When you encrypt messages or check signatures, it's super important to know that the public key you're using really belongs to the person you think it does. Just downloading a public key from the internet isn't always safe, as someone could pretend to be someone else.
PGP has a system called the "web of trust." This idea was first described by Phil Zimmermann in 1992. It means that people can digitally "sign" other people's public keys to say, "I trust that this key belongs to this person." Over time, as more people sign keys, a network of trust grows. It's like friends introducing you to their friends, and you trust the new friends because your original friends vouched for them. This system is different from others that rely on a central authority to say who is trustworthy.
Key Certificates and Their Use
In the OpenPGP system, there are also "trust signatures" that can help create what are called "certificate authorities." A trust signature means that the key belongs to its owner and that the owner can be trusted to sign other keys.
PGP has always had a way to cancel public key certificates if a private key is lost or stolen. This is important for keeping communications secure. Newer PGP versions also allow keys to have expiration dates.
The challenge of making sure a public key truly belongs to a specific person is not just a PGP problem; it's a challenge for all systems that use public and private keys. PGP's original system lets users decide how much they want to trust others' endorsements, which is different from many other systems that require you to trust a central authority.
How Secure is PGP?
Based on what we know, there's no public method to break PGP encryption using typical computer power or code-breaking techniques. In 1995, a famous expert named Bruce Schneier even said an early version was "the closest you're likely to get to military-grade encryption." While some older PGP versions had small theoretical weaknesses, current versions are much stronger. PGP can protect data not only when it's being sent over a network but also when it's stored on a computer or hard drive.
The strength of PGP encryption relies on the idea that the math and algorithms it uses are too hard to break with today's technology. New versions of PGP are released regularly, and any weaknesses found are quickly fixed by the developers.
PGP's Journey Through Time
The Beginning
Phil Zimmermann created the very first version of PGP in 1991. The name "Pretty Good Privacy" was inspired by a grocery store from a radio show. Zimmermann, who was involved in the anti-nuclear movement, wanted to create PGP so that people could communicate and store messages securely. He made it free for non-commercial use and even included the full source code.
PGP quickly spread across the internet and gained many followers worldwide. People who wanted more privacy, like activists and civil rights supporters, found it very useful.
Legal Challenges and Freedom of Speech
Soon after its release, PGP made its way outside the United States. In 1993, Zimmermann faced a criminal investigation from the US government. At that time, encryption software with strong keys was considered "munitions" (like weapons) and had strict export rules. PGP used strong keys, so it was caught in these rules. After several years, the investigation was closed without charges.
Zimmermann famously challenged these rules in a creative way. In 1995, he published the entire source code of PGP in a book. His idea was that exporting a book, which is protected by freedom of speech, should be different from exporting a weapon. While this specific case wasn't fully tested in court, later court rulings did say that computer code can be a form of speech protected by the First Amendment.
US export rules for encryption became much more relaxed in the late 1990s. By 2000, PGP was no longer considered a non-exportable weapon and could be sent internationally, except to a few specific countries or groups.
PGP Inc. and New Versions
After the investigation ended in 1996, Zimmermann and his team started a company called PGP Inc. to create new versions of the software. They worked on PGP 3, which had better security and new features. This version was designed to be more flexible, allowing users to work with it through commands or a graphical interface. PGP 3 was later released as PGP 5 in May 1997.
Changes in Ownership
In December 1997, a company called Network Associates, Inc. (NAI) bought PGP Inc. Zimmermann and his team became NAI employees. Under NAI, the PGP family of products grew to include disk encryption and other security tools.
Later, in 2001, Zimmermann left NAI. In October 2001, NAI announced it was selling its PGP assets and stopping further development of most PGP products.
McAfee and SDS
NAI, which later became McAfee, continued to sell a command-line version of PGP until 2013. This product was then transferred to Software Diversified Services (SDS), which still sells and develops it today as SDS E-Business Server.
PGP Corporation
In August 2002, some former PGP team members started a new company called PGP Corporation. They bought most of the PGP products from NAI. PGP Corporation continued to support existing PGP users. Zimmermann also worked as an advisor for the new company. PGP Corporation developed new products, including PGP Universal, a server-based tool for managing encryption.
Symantec Takes Over
On April 29, 2010, Symantec Corp. announced it would buy PGP Corporation. This deal was completed on June 7, 2010. Symantec integrated PGP into its security products.
In May 2018, a bug called EFAIL was found in some PGP setups. This bug could, in certain situations, reveal the content of encrypted emails. Symantec updated its PGP Desktop software to fix this.
Broadcom's Acquisition
On August 9, 2019, Broadcom Inc. announced it would acquire Symantec's Enterprise Security software division, which included the PGP products.
PGP Encryption Applications
PGP products have grown a lot since 2002. While PGP was first mainly used for encrypting emails, it now offers many different encryption tools. These tools can be managed by a central server. PGP encryption applications can secure emails, digital signatures, entire computer disks, files, and folders. They can also protect instant messages and help with secure file transfers.
For example, PGP Desktop 9.x included tools like PGP Desktop Email, PGP Whole Disk Encryption, and PGP NetShare. These tools offered features like email security, digital signatures, and full disk encryption.
The PGP Universal Server helps manage all these PGP applications from one central place. It handles things like deploying the software, setting security rules, managing keys, and reporting. It can also work with the PGP Global Directory, which is a public keyserver, to find recipient keys.
Newer versions of PGP software, like PGP Desktop 9.x managed by PGP Universal Server 2.x (released in 2005), use a new system that makes them easier to use and more automated. The PGP Universal server automatically creates, manages, and expires keys, sharing them across all PGP applications.
Today, Symantec PGP Desktop is known as Symantec Encryption Desktop (SED), and PGP Universal Server is called Symantec Encryption Management Server (SEMS).
There's also PGP Command-Line, which lets you encrypt and sign information using text commands. And the PGP Support Package for BlackBerry helps secure messages on BlackBerry devices.
Modern PGP applications use both OpenPGP and S/MIME standards, allowing them to communicate securely with many different users.
OpenPGP Standard
Because PGP was so important worldwide, many people wanted to create their own software that could work with PGP. In July 1997, PGP Inc. suggested to the IETF (Internet Engineering Task Force) that there should be an "OpenPGP" standard. They gave the IETF permission to use the name. The IETF agreed and started working on the OpenPGP standard.
OpenPGP is an official internet standard that is still being updated. Many email programs use OpenPGP to provide secure email. The current version of the standard is RFC 9580 (from July 2024). This version specifies certain required algorithms, like X25519 and AES-128, and recommends others.
OpenPGP encryption helps ensure that files and messages are delivered securely. It also verifies who created or sent a message using digital signing. The open source office suite LibreOffice added the ability to sign documents with OpenPGP in version 5.4.0 on Linux. OpenPGP can also protect sensitive files stored on mobile devices or in the cloud.
In late 2023, there was a disagreement within the OpenPGP community about how to update the standard. This led to one of the main developers of GnuPG, Werner Koch, creating his own separate specification called "LibrePGP."
OpenPGP Programs
The Free Software Foundation developed its own OpenPGP-compatible software called GNU Privacy Guard (GnuPG). It's free and comes with all its source code. Many other programs, like Mozilla Thunderbird (which has built-in support since version 78), GitHub, and GitLab, also support PGP keys. There's even an OpenPGP library written in JavaScript called OpenPGP.js, which allows web-based applications to use PGP encryption right in your web browser.
Things to Consider About PGP
While PGP and OpenPGP are very strong, some people have pointed out areas that could be improved:
- PGP public keys can be quite long.
- It doesn't always offer "forward secrecy," which means if a key is ever compromised, past communications might also be at risk.
- Some older versions or default settings might use algorithms that are not as strong as the newest ones.
- It can be difficult for new users to understand and use.
- It's not used by everyone, so you might not always be able to use it with everyone you communicate with.
In October 2017, a security flaw called the ROCA vulnerability was found. This affected RSA keys created by certain hardware, like some Yubikey tokens, which are often used with OpenPGP. Many PGP keys were found to be at risk, and the company Yubico offered free replacements for affected tokens.
See also
 In Spanish: Pretty Good Privacy para niños
In Spanish: Pretty Good Privacy para niños
- Electronic envelope
- Email encryption
- Email privacy
- GNU Privacy Guard
- Gpg4win
- Key server (cryptographic)
- PGP word list
- PGPDisk
- Pretty Easy privacy
- Privacy software
- Public-key cryptography
- S/MIME
- X.509
- ZRTP
 | Claudette Colvin |
 | Myrlie Evers-Williams |
 | Alberta Odell Jones |