ARP spoofing facts for kids
In computer networking, ARP spoofing (also called ARP cache poisoning or ARP poison routing) is a trick used by an attacker. They send fake messages called ARP messages onto a local area network (LAN).
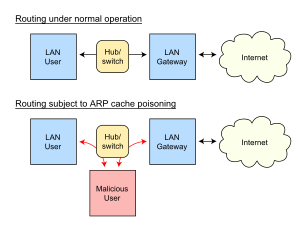
Think of a LAN like a neighborhood where computers talk to each other. Each computer has a special address called an IP address (like a street address) and another address called a MAC address (like a house number). When one computer wants to send data to another, it uses ARP to find out the MAC address for a known IP address.
With ARP spoofing, the attacker tries to link their own MAC address to the IP address of another computer. This other computer might be an important one, like the "default gateway" (which is like the main post office for the network). When this happens, any data meant for that important computer gets sent to the attacker instead.
ARP spoofing can let an attacker secretly look at the data on a network, change the data, or even stop all data from flowing. This attack is often used as a first step for other attacks, such as denial of service (stopping services), man-in-the-middle (spying and changing data), or session hijacking (taking over someone's online session).
This trick only works on networks that use ARP. The attacker also needs to be directly connected to the part of the network they want to attack.
Contents
How ARP Works (and Why It's Tricked)
The Address Resolution Protocol (ARP) is a common way for computers to find each other's physical addresses (MAC addresses) when they only know their internet addresses (IP addresses).
When a computer wants to send data to another computer on the same local area network, it needs to know the other computer's MAC address. If it doesn't know, it sends out a special message called an ARP request to everyone on the network. This request asks, "Who has this IP address? Tell me your MAC address!"
The computer with that IP address then sends back an ARP reply message. This reply contains its MAC address.
The problem is that ARP is a "stateless protocol." This means computers don't check if the ARP replies they get are real or if they asked for them. They just automatically save any ARP replies they receive. Even if a computer already has an ARP entry saved, a new ARP reply will overwrite it. There's no way for a computer to check if the message came from the real computer it claims to be. This is the weakness that allows ARP spoofing to happen.
How the Attack Happens
The main idea behind ARP spoofing is to use the weakness in the ARP system by sending fake ARP messages onto the network. An attacker can do this from a computer they have taken control of on the network, or from their own computer connected to the target network.
An attacker using ARP spoofing pretends to be another computer to get in the middle of data being sent. The computers sending data won't know that the attacker is not the real computer they think they are talking to.
Usually, the attacker wants to link their own computer's MAC address with the IP address of a target computer. This way, any data meant for the target computer will go to the attacker's computer instead. The attacker can then:
- Spy: Look at the data without changing it. They might then send the data on to its real destination so no one notices.
- Change Data: Modify the data before sending it to its real destination (this is a man-in-the-middle attack).
- Stop Data: Launch a denial-of-service attack by making some or all of the data on the network disappear.
How to Defend Against ARP Spoofing
Setting Fixed ARP Entries
One simple way to protect against ARP spoofing is to use "static" (fixed) entries in a computer's ARP memory (called the ARP cache). For important network services, you can manually enter the IP address and MAC address pairs. This way, computers don't need to send out ARP requests for these services.
While this helps, it can be a lot of work to set up and manage, especially on a large network. You would need to set up a fixed entry for every other computer on each computer, which can become very complicated.
Detection and Prevention Software
Software designed to detect ARP spoofing usually checks ARP responses to make sure they are real. If an ARP response seems fake, the software blocks it. These tools can work with DHCP servers (which give out IP addresses) to make sure both temporary and permanent IP addresses are checked.
This protection can be on individual computers or built into network devices like Ethernet switches. If a single MAC address suddenly has many IP addresses linked to it, it could mean an ARP spoofing attack is happening. Some tools just listen for ARP replies and send an email alert if an ARP entry changes.
Some operating systems like OpenBSD also watch for computers pretending to be local hosts and warn if someone tries to change a permanent entry.
Operating System Security
Different operating systems handle ARP differently. For example, Linux usually ignores ARP replies it didn't ask for, but it might use replies to requests from other computers to update its memory. Microsoft Windows lets you change how its ARP memory works through special settings.
Good Uses for ARP Tricks
The same techniques used in ARP spoofing can also be used for good reasons, like making network services more reliable. For example, some software allows a backup server to send a special ARP message to take over if the main server breaks down. This makes sure services keep running smoothly without anyone noticing a problem.
Developers also use ARP tricks to check how data is flowing between two computers when they are connected through a network switch. Normally, a third computer can't see this traffic. But by using ARP spoofing, the developer can make both computers send their data through the monitoring computer. This lets the developer see and understand the data flow, just like in a man-in-the-middle attack, but for a good purpose.
Tools for ARP Spoofing and Defense
Defense Tools
| Name | OS | GUI | Free | Protection | Per interface | Active/passive | Notes |
|---|---|---|---|---|---|---|---|
| Agnitum Outpost Firewall | Windows | Yes | No | Yes | No | passive | |
| AntiARP | Windows | Yes | No | Yes | No | active+passive | |
| Antidote | Linux | No | Yes | No | ? | passive | A Linux program that watches network mappings and looks for unusual numbers of ARP packets. |
| Arp_Antidote | Linux | No | Yes | No | ? | passive | A Linux Kernel Patch that watches network mappings and can be set to take action. |
| Arpalert | Linux | No | Yes | No | Yes | passive | Uses a list of allowed MAC addresses and sends an alert if a MAC address not on the list appears. |
| ArpON | Linux | No | Yes | Yes | Yes | active+passive | A program that helps secure ARP against spoofing attacks in different types of networks. |
| ArpGuard | Mac | Yes | No | Yes | Yes | active+passive | |
| ArpStar | Linux | No | Yes | Yes | ? | passive | |
| Arpwatch | Linux | No | Yes | No | Yes | passive | Keeps track of IP-MAC address pairs and reports changes through system logs or email. |
| ArpwatchNG | Linux | No | Yes | No | No | passive | Keeps track of IP-MAC address pairs and reports changes through system logs or email. |
| Colasoft Capsa | Windows | Yes | No | No | Yes | no detection, only analysis with manual inspection | |
| cSploit | Android (rooted only) | Yes | Yes | No | Yes | passive | |
| elmoCut | Windows | Yes | Yes | No | ? | passive | |
| Prelude IDS | ? | ? | ? | ? | ? | ? | Has an ArpSpoof plugin that performs basic checks on addresses. |
| Panda Security | Windows | ? | ? | Yes | ? | Active | Performs basic checks on addresses. |
| remarp | Linux | No | Yes | No | No | passive | |
| Snort | Windows/Linux | No | Yes | No | Yes | passive | A Snort tool that performs basic checks on addresses. |
| Winarpwatch | Windows | No | Yes | No | No | passive | Keeps track of IP-MAC address pairs and reports changes through system logs or email. |
| XArp | Windows, Linux | Yes | Yes (+pro version) | Yes (Linux, pro) | Yes | active + passive | Advanced detection for ARP spoofing, with active checks and passive monitoring. Has two user interfaces. |
| Seconfig XP | Windows 2000/XP/2003 only | Yes | Yes | Yes | No | only activates protection built-in some versions of Windows | |
| zANTI | Android (rooted only) | Yes | Yes | No | ? | passive | |
| NetSec Framework | Linux | No | Yes | No | No | active | |
| anti-arpspoof | Windows | Yes | Yes | ? | ? | ? | |
| DefendARP: | ? | ? | ? | ? | ? | ? | A tool for monitoring and defending against ARP attacks, especially on public Wi-Fi. It finds attacks, fixes the problem, and identifies the attacker. |
| NetCutDefender: | Windows | ? | ? | ? | ? | ? | A graphical tool for Windows that can protect against ARP attacks. |
Spoofing Tools
Here are some tools that can be used to carry out ARP spoofing attacks:
- Arpspoof (part of the DSniff tools)
- Arpoison
- Subterfuge
- Ettercap
- Seringe
- ARP-FILLUP -V0.1
- arp-sk -v0.0.15
- ARPOc -v1.13
- arpalert -v0.3.2
- arping -v2.04
- arpmitm -v0.2
- arpoison -v0.5
- ArpSpyX -v1.1
- ArpToXin -v 1.0
- Cain and Abel -v 4.3
- cSploit -v 1.6.2
- SwitchSniffer
- APE – ARP Poisoning Engine
- Simsang
- zANTI -v2
- elmoCut
- NetSec Framework -v1
- Minary
- NetCut (also has a defense feature)
- ARPpySHEAR
See also
 In Spanish: Suplantación de ARP para niños
In Spanish: Suplantación de ARP para niños
- Cache poisoning
- DNS spoofing
- IP address spoofing
- MAC spoofing
- Proxy ARP