Denial-of-service attack facts for kids
In the world of computing, a denial-of-service attack (often called a DoS attack) is a type of cyber-attack. It's when someone tries to stop a computer or network from working for its normal users. This can be done by making the service unavailable for a short time or even forever. DoS attacks usually work by sending too many requests to a target. This overloads the system and stops real users from getting through. Attacks can range from sending millions of requests to slow things down, to sending bad data, or using fake IP addresses.
A distributed denial-of-service attack (DDoS attack) is a bigger version of this. Here, the flood of traffic comes from many different places. This makes it much harder to stop. You can't just block one source because there are many. Think of it like a huge crowd blocking the entrance to a shop. Real customers can't get in, so the shop loses money. People who do these attacks often target big websites like banks or credit card payment sites. They might do it for revenge, to blackmail someone, or for hacktivism (using hacking for a cause).
Contents
- History of DoS Attacks
- Types of DoS Attacks
- Symptoms of a DoS Attack
- Attack Techniques
- Attack Tools
- HTTP Slow POST DoS Attack
- Challenge Collapsar (CC) Attack
- Internet Control Message Protocol (ICMP) Flood
- Nuke
- Peer-to-Peer Attacks
- Permanent Denial-of-Service Attacks
- Reflected Attacks
- Mirai Botnet
- R-U-Dead-Yet? (RUDY)
- Slow Read Attack
- Sophisticated Low-Bandwidth Distributed Denial-of-Service Attack
- SYN Flood
- Teardrop Attacks
- Telephony Denial-of-Service
- UPnP Attack
- SSDP Reflection Attack
- ARP Spoofing
- Defense Techniques
- Unintentional Denial-of-Service
- Side Effects of Attacks
- Legality
- See also
History of DoS Attacks
One of the first DoS attacks happened on September 6, 1996. It targeted Panix, an early ISP. This attack, called a SYN flood, shut down their services for several days. In 1997, Khan C. Smith showed another early DoS attack. He disrupted internet access in Las Vegas Strip for over an hour. Later, sample code from this event led to attacks on big companies like Sprint and EarthLink.
The biggest DDoS attack known happened in September 2017. Google Cloud was hit with a massive attack. It reached a peak of 2.54 Tb/s. This was revealed by Google in 2020. Another huge attack in February 2020 hit Amazon Web Services. It peaked at 2.3 Tb/s. In July 2021, Cloudflare protected a client from a DDoS attack. This attack came from a global Mirai botnet and sent 17.2 million requests per second.
In 2022, the Russian invasion of Ukraine led to many cyberattacks. Ukraine faced its largest DDoS attack in February. This disrupted government and financial services. Other countries like the UK, US, and Germany also saw more attacks. In February 2023, Cloudflare faced another record-breaking attack. It sent 71 million requests per second. In October 2023, new weaknesses in the HTTP/2 protocol led to even bigger attacks. One attack reached 398 million requests per second.
Types of DoS Attacks
DoS attacks are all about stopping people from using a service. There are two main types: those that crash services and those that flood them. The most serious ones are "distributed" attacks.
Distributed Attacks
A distributed denial-of-service (DDoS) attack happens when many computer systems work together. They flood the bandwidth or resources of a target system. This is usually aimed at one or more web servers. A DDoS attack uses many different IP addresses or computers. Often, these are thousands of computers infected with malware. A DDoS attack usually involves more than 3-5 computers on different networks.
Many machines can create more attack traffic than just one. It's also harder to stop many attack machines than just one. Each attack machine can also be more hidden. This makes it tough to find and shut them down. Since the traffic comes from many places, blocking a single source doesn't work. It also makes it hard to tell real users from attackers. Attackers might also use fake IP addresses (IP address spoofing). This makes it even harder to find them. DDoS attacks have grown much larger over the years. Some common DDoS attacks include UDP flooding, SYN flooding, and DNS amplification.
Yo-yo Attack
A yo-yo attack is a special type of DoS/DDoS attack. It targets apps that use cloud computing and can automatically grow or shrink their resources (autoscaling). The attacker sends a lot of traffic. This makes the cloud service grow to handle the traffic. Then, the attacker stops the attack. This leaves the victim with too many resources, which costs them money. When the victim shrinks their resources, the attack starts again. This causes problems when the service is scaling up and down. It also costs the victim money, while costing the attacker less.
Application Layer Attacks
An application layer DDoS attack (also called a layer 7 DDoS attack) targets specific parts of a website. Attackers try to overload certain features or functions of a site. This is different from attacking the whole network. These attacks are often used against financial companies. They can distract IT and security teams from other problems. In 2013, these attacks made up 20% of all DDoS attacks. By 2017, network attacks were less common, but application-layer attacks were still happening a lot.
What is the Application Layer?
The OSI model is a way to understand how computer systems talk to each other. It divides communication into seven layers. The application layer is like the user interface. It shows data and images to you in a way you can understand. It also connects with the layer below it. In real life, the application and presentation layers are often combined.
How Application Layer Attacks Work
The simplest DoS attack uses brute force. It floods the target with so many packets that it overloads its internet connection. Or, it uses up all the target's computer resources. To do this, attackers often use a botnet. A botnet is a network of infected computers. An application layer DDoS attack is usually for specific goals. These include stopping transactions or access to databases. It needs fewer resources than network attacks. But it often happens along with them. The attack might look like normal traffic. But it targets specific parts of the application. This can stop things like searching or getting information from a website.
Advanced Persistent DoS
An advanced persistent DoS (APDoS) is a very serious and long-lasting attack. It can go on for weeks. The longest one known lasted 38 days. This attack involved huge amounts of bad traffic. Attackers might switch between targets to confuse defenses. But they always focus on one main victim. These attackers have access to very powerful network resources. They can keep up a long attack with huge amounts of traffic. APDoS attacks involve:
- Looking around first: Attackers gather information before the attack. They try to avoid being noticed.
- Smart attacks: They attack both main and secondary targets. But the main target is the focus.
- Clear goals: They have a specific reason or goal for the attack.
- Lots of computing power: They have access to powerful computers and internet connections.
- Attacks on many levels: They use complex tools that attack different parts of the network at the same time.
- Long-lasting: They combine all these things into a planned, ongoing attack.
Denial-of-Service as a Service
Some people offer "booter" or "stresser" services online. These are simple websites where you can pay to launch a DoS attack. They are advertised as tools to test how strong a network is. But they can be used to perform illegal DoS attacks. They let people who aren't tech experts use advanced attack tools. These services are usually powered by a botnet. The traffic they create can be big enough to stop an average home user from using the internet.
Symptoms of a DoS Attack
The United States Computer Emergency Readiness Team (US-CERT) says these are signs of a DoS attack:
- Your internet connection is unusually slow (like when opening files or websites).
- A specific website is not working.
- You can't access any websites at all.
Attack Techniques
Attack Tools
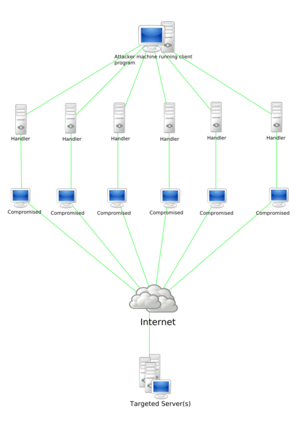
Sometimes, attack tools are hidden inside malware. This means they launch attacks without the computer owner knowing. Stacheldraht is an old example of a DDoS tool. It uses a layered system. The attacker connects to "handlers" (compromised computers). These handlers then tell "zombie agents" (more compromised computers) to start the DDoS attack. These agents are infected by the handlers. Each handler can control up to a thousand agents.
Other times, a computer might join a DDoS attack with the owner's permission. For example, in Operation Payback, organized by the group Anonymous. Tools like the Low Orbit Ion Cannon are often used this way. There are many DDoS tools available today, both free and paid. They have different features. There's even an underground market for them among hackers.
HTTP Slow POST DoS Attack
First found in 2009, the HTTP slow POST attack sends a normal HTTP POST header. This header tells the server how big the message body will be. But then, the attacker sends the actual message body very, very slowly. For example, one byte every 110 seconds. The server waits for the whole message to arrive, which takes a very long time. The attacker opens hundreds or thousands of these slow connections. This uses up all the server's resources for new connections. This stops anyone else from connecting. This attack is hard to spot because it looks like normal traffic.
Challenge Collapsar (CC) Attack
A Challenge Collapsar (CC) attack sends many standard HTTP requests to a web server. The requests target parts of the website that need complex calculations or database work. This can use up all the web server's resources. In 2004, a Chinese hacker named KiKi created a tool for this. He used it to attack a firewall called Collapsar. That's how this type of attack got the name "CC attack."
Internet Control Message Protocol (ICMP) Flood
A smurf attack uses network devices that are set up incorrectly. These devices let packets be sent to all computers on a network, not just one. The attacker sends many IP packets. They fake the source address to be the victim's address. Most devices on the network will reply to this. They send a response back to the fake source IP address. If many machines on the network reply, the victim's computer gets flooded with traffic. This overloads the victim's computer and can make it unusable.
A ping flood sends a huge number of ping packets to the victim. This is simple to do. The main thing needed is more internet speed than the victim. A ping of death sends a badly formed ping packet. This can crash a vulnerable system. The BlackNurse attack is another example. It uses special ICMP packets to overload the target.
Nuke
A nuke is an older type of DoS attack. It sends broken or invalid ICMP packets to a target. This is done using a changed ping tool. It repeatedly sends this bad data. This slows down the affected computer until it stops completely. One famous nuke attack was WinNuke. It used a weakness in Windows 95. It sent special data to TCP port 139. This made the computer freeze and show a Blue Screen of Death.
Peer-to-Peer Attacks
Attackers have found ways to use problems in peer-to-peer servers to start DDoS attacks. The most aggressive of these uses DC++. In these attacks, there is no botnet. The attacker doesn't need to talk to the computers they control. Instead, the attacker acts like a "puppet master." They tell users of large peer-to-peer file sharing networks to disconnect from their network. Then, they tell them to connect to the victim's website instead.
Permanent Denial-of-Service Attacks
Permanent denial-of-service (PDoS) attacks are also called phlashing. This attack damages a system so badly that it needs new hardware or a complete reinstallation. Unlike a DDoS attack, a PDoS attack uses security flaws. These flaws let attackers control the management parts of a victim's hardware. This includes things like routers, printers, or other networking hardware. The attacker uses these vulnerabilities to replace the device's firmware with bad or broken firmware. This process is called "flashing" when done correctly. The goal is to "brick" the device. This means it becomes unusable until it's fixed or replaced. PDoS is a hardware-focused attack. It can be much faster and needs fewer resources than a DDoS attack using a botnet.
Reflected Attacks
A distributed denial-of-service attack can involve sending fake requests to many computers. These computers will then reply to the requests. By using Internet Protocol address spoofing, the attacker sets the source address to be the victim's address. This means all the replies go to (and flood) the victim. This type of attack is sometimes called a distributed reflective denial-of-service (DRDoS) attack. ICMP echo request attacks (Smurf attacks) are a type of reflected attack. The attacking computers send Echo Requests to the broadcast addresses of networks that are set up incorrectly. This makes many computers send Echo Reply packets to the victim.
Amplification
Amplification attacks make the amount of data sent to a victim much larger. Many services can be used to reflect and amplify attacks. Some are harder to block than others. US-CERT has seen that different services can increase the attack size by different amounts. For example, a small request to a NTP server can result in a response 556.9 times larger. This happens if the server is set up to send details of recent requests. When many botnet computers send these small requests with the victim's fake IP address, a huge amount of data is sent to the victim. It's hard to stop these attacks because the data comes from real servers. These requests also use UDP, which doesn't check the sender's IP address.
Mirai Botnet
The Mirai botnet works by infecting hundreds of thousands of IoT devices. These are devices like smart thermostats, Wi-Fi clocks, and washing machines. The worm spreads through networks and takes control of poorly protected IoT devices. The owner usually doesn't know their device is infected. The IoT device itself isn't the target. It's used as part of a bigger attack. Once the hacker has enough devices, they tell them to attack a target. In October 2016, a Mirai botnet attacked Dyn. Dyn is an ISP for sites like Twitter and Netflix. These websites became unreachable for several hours.
R-U-Dead-Yet? (RUDY)
The RUDY attack targets web applications. It tries to use up all the available connections on the web server. Like Slowloris, RUDY keeps connections open by sending very slow, never-ending POST messages. It sends a very large "content-length" value in the header.
Slow Read Attack
A slow read attack sends normal requests to an application. But it reads the responses very slowly. This keeps connections open longer. The goal is to use up all the server's connection slots. The slow read happens by telling the server to send only a very small amount of data at a time. This makes the data flow rate very low.
Sophisticated Low-Bandwidth Distributed Denial-of-Service Attack
A sophisticated low-bandwidth DDoS attack uses less traffic. It becomes effective by targeting a weak point in the victim's system. The attacker sends traffic with complex requests to the system. This type of attack costs less because it uses less traffic. It's also smaller, making it harder to spot. And it can hurt systems that have flow control defenses.
SYN Flood
A SYN flood happens when a computer sends many TCP/SYN packets. Often, these packets have a fake sender address. Each packet is treated like a connection request. This makes the server create a "half-open connection." The server sends back a TCP/SYN-ACK packet and waits for a reply. But because the sender's address is fake, the reply never comes. These half-open connections use up all the server's available connections. This stops it from responding to real requests until the attack ends.
Teardrop Attacks
A teardrop attack sends broken IP fragments to the target computer. These fragments have overlapping or too-large data. This can crash some operating systems. It's due to a problem in how they put together fragmented TCP/IP packets. Older versions of Windows 3.1x, Windows 95, Windows NT, and some Linux versions were vulnerable. An IP header has a "fragment offset" field. This shows where the data in a fragmented packet starts. If the parts of a packet overlap, a server vulnerable to teardrop attacks can't put them back together. This causes a denial-of-service.
Telephony Denial-of-Service
Voice over IP (VoIP) makes it cheap and easy to make many phone calls automatically. It also lets people fake their caller ID. According to the US Federal Bureau of Investigation, telephony denial-of-service (TDoS) has been used in scams:
- A scammer pretends to be the victim to their bank. They ask for a money transfer. The bank tries to call the victim to check. But the victim's phone lines are flooded with fake calls. So, the victim can't be reached.
- A scammer calls people with a fake debt claim. If the person refuses, the scammer floods the victim's employer with automated calls. Sometimes, the caller ID is faked to look like police.
- Swatting: A scammer calls people with a fake debt demand. They threaten to send police. If the victim refuses, the scammer floods local police numbers with calls. The caller ID is faked to show the victim's number. Police then show up at the victim's home.
TDoS can happen even without internet phones. In 2002, during a New Hampshire election, telemarketers flooded opponents' phone lines. This jammed them on election day. If a phone number is widely shared, it can also get flooded with calls. This happened by accident in 1981 with the song "867-5309/Jenny". TDoS is different from other telephone harassment because of the huge number of calls. By keeping lines busy with automated calls, the victim can't make or get calls, even emergency ones. Related attacks include SMS flooding and continuous fax transmissions.
UPnP Attack
A UPnP attack uses a weakness in the Universal Plug and Play (UPnP) protocol. This lets attackers bypass network security. They can then flood a target's network and servers. The attack is like a DNS amplification attack. But it uses a UPnP router. This router forwards requests from one outside source to another. The UPnP router sends data back on an unexpected UDP port from a fake IP address. This makes it harder to stop the traffic flood. Experts say the best way to stop this is to secure UPnP routers.
SSDP Reflection Attack
In 2014, it was found that Simple Service Discovery Protocol (SSDP) was used in DDoS attacks. These were called SSDP reflection attacks with amplification. Many devices, including home routers, have a flaw in their UPnP software. This allows an attacker to get replies from UDP port 1900 to any address they choose. With a botnet of thousands of devices, attackers can send enough packets to overload internet connections. This causes services to stop working. Because of this weakness, Cloudflare called SSDP the "Stupidly Simple DDoS Protocol."
ARP Spoofing
ARP spoofing is a common DoS attack. It uses a weakness in the ARP protocol. This allows an attacker to link their computer's MAC address to another computer's or gateway's IP address. This makes traffic meant for the real IP address go to the attacker instead. This causes a denial of service.
Defense Techniques
Defending against denial-of-service attacks usually involves a mix of tools. These tools detect attacks, sort traffic, and block what they see as bad traffic. They also allow good traffic to pass through. Here are some ways to defend against these attacks.
Upstream Filtering
All internet traffic going to the victim is sent through a "cleaning center." This center removes "bad" traffic, like DDoS attacks. It only sends good, real traffic to the victim's server. The victim needs a good internet connection to use this service. DDoS attacks can overwhelm any hardware firewall. Sending bad traffic through large, strong networks is becoming more effective and affordable against DDoS.
Application Front End Hardware
This is smart hardware placed on the network before traffic reaches the servers. It works with routers and switches. It also helps manage internet speed. This hardware checks data packets as they enter the network. It finds and drops dangerous or suspicious traffic.
Application Level Key Completion Indicators
One way to find DDoS attacks on cloud apps is to look at the application layer. This checks if incoming traffic is real. These methods look at how requests move through the application. They use "key completion indicators" to track progress. Basically, these are ways to statistically check if incoming requests are behaving strangely. Imagine a store where customers usually spend time looking at items, putting them back, and then buying things. If a huge group of people came in and only looked at items but never bought anything, that would be unusual.
Blackholing and Sinkholing
With blackhole routing, all traffic to the attacked DNS or IP address is sent to a "black hole." This is a null interface or a server that doesn't exist. To be more effective, your internet provider can manage this. A DNS sinkhole sends traffic to a real IP address. This address then checks the traffic and blocks bad packets. Sinkholing might not work well for very big attacks.
IPS Based Prevention
Intrusion prevention systems (IPS) work well if attacks have known patterns. However, many new attacks look like normal traffic but have bad intentions. IPS systems that only recognize content can't block behavior-based DoS attacks. An ASIC-based IPS can find and block DoS attacks. They have the power to analyze attacks and act like a circuit breaker automatically.
DDS Based Defense
A DoS defense system (DDS) is made specifically for DoS attacks. It can block connection-based DoS attacks. It also blocks attacks that look like normal traffic but have bad intentions. A DDS can handle attacks that break rules (like teardrop) and attacks that send too much data (like ICMP floods). A DDS has a special system that can find and stop denial-of-service attacks faster than software.
Firewalls
For a simple attack, a firewall can be set to block all incoming traffic from the attackers. This can be based on rules about protocols, ports, or IP addresses. But more complex attacks are hard to block with simple rules. For example, if port 80 (web service) is under attack, you can't just block all traffic on that port. This would stop real users too. Also, firewalls might be too far down in the network. Routers might be affected before the traffic even reaches the firewall. Many security tools also don't support IPv6 or are not set up correctly. This means firewalls can be bypassed during attacks.
Routers
Like switches, routers have some ways to limit traffic and control access. These are usually set manually. Most routers can be easily overwhelmed during a DoS attack. Some advanced routers offer DDoS protection. Cisco IOS has features that can help reduce the impact of flooding.
Switches
Most switches can limit traffic and control access. Some switches can automatically limit traffic, shape traffic, and inspect packets deeply. They can also filter fake IP addresses. This helps them find and stop DoS attacks. For example, a SYN flood can be stopped by delaying connections. Attacks that use bad packets can be stopped by filtering them. Automatic traffic limiting works if the limits are set correctly.
Blocking Vulnerable Ports
For example, in an SSDP reflection attack, the main way to stop it is to block incoming UDP traffic on port 1900 at the firewall.
Unintentional Denial-of-Service
An unintentional denial-of-service happens when a system stops working. This isn't because of a planned attack. It's simply because of a sudden, huge increase in popularity. This can happen when a very popular website links to a smaller, less prepared site. For example, as part of a news story. Many users from the big site might click the link at once. This has the same effect on the target website as a DDoS attack. A VIPDoS is similar, but it happens when a celebrity posts the link. When Michael Jackson died in 2009, sites like Google and Twitter slowed down or crashed. Many servers thought the requests were from a virus. They warned users that their searches looked like "automated requests from a computer virus or spyware application."
News sites and link sites are most likely to cause this. A famous example is the Slashdot effect when getting traffic from Slashdot. It's also known as "the Reddit hug of death" or "the Digg effect." Routers have also caused unintentional DoS attacks. Both D-Link and Netgear routers have overloaded NTP servers. They flooded them without following rules about client types or locations.
Legal action has been taken in some cases. In 2006, Universal Tube & Rollform Equipment Corporation sued YouTube. Many people trying to go to YouTube.com accidentally typed utube.com. This made the tube company spend a lot of money on upgrading its internet speed. The company now uses utube.com for ads. In March 2014, after Malaysia Airlines Flight 370 went missing, DigitalGlobe launched a service. Users could help search for the jet in satellite images. The response overwhelmed the company's servers. An unintentional denial-of-service can also happen from a planned event by the website itself. This happened with the Census in Australia in 2016.
Side Effects of Attacks
Backscatter
In computer security, backscatter is a side effect of a fake denial-of-service attack. In this attack, the attacker fakes the source address in IP packets sent to the victim. The victim's computer usually can't tell the difference between fake and real packets. So, the victim replies to the fake packets as it normally would. These reply packets are called backscatter.
If the attacker is faking source addresses randomly, the backscatter replies from the victim will go to random places. This effect can be used by "network telescopes." These are tools that watch internet traffic. They use backscatter as indirect proof of such attacks. "Backscatter analysis" means watching backscatter packets. This helps figure out how DoS attacks happen and who the victims are.
Legality
Many countries have laws that make denial-of-service attacks illegal. The UNCTAD says that 156 countries, or 80% worldwide, have laws against cybercrime. This is to fight its widespread impact.
- In the US, denial-of-service attacks can be a federal crime. Penalties can include years in prison. The Computer Crime and Intellectual Property Section of the US Department of Justice handles these cases. For example, in July 2019, Austin Thompson was sentenced to 27 months in prison. He also had to pay $95,000 for DDoS attacks on video game companies.
- In European countries, doing criminal denial-of-service attacks can lead to arrest. The United Kingdom specifically made DoS attacks illegal. The maximum penalty is 10 years in prison.
- In January 2019, Europol announced that they were tracking down users of Webstresser.org. This was a DDoS marketplace that was shut down in April 2018. Europol said UK police were targeting over 250 users of Webstresser and other DDoS services.
On January 7, 2013, Anonymous asked the US government to recognize DDoS as a legal form of protest. They said it was similar to the Occupy protests.
See also
 In Spanish: Ataque de denegación de servicio para niños
In Spanish: Ataque de denegación de servicio para niños
- BASHLITE
- Billion laughs attack
- Black fax
- Botnet
- Blaster (computer worm)
- Clear channel assessment attack
- Dendroid (malware)
- Distributed denial-of-service attacks on root nameservers
- DNS Flood
- Fork bomb
- High Orbit Ion Cannon (HOIC)
- Hit-and-run DDoS
- Industrial espionage
- Infinite loop
- Intrusion detection system
- Killer poke
- Lace card
- Low Orbit Ion Cannon (LOIC)
- Mixed threat attack
- Network intrusion detection system
- 2016 Dyn cyberattack
- Operation PowerOFF
- Paper terrorism
- Project Shield
- ReDoS
- Resource exhaustion attack
- SlowDroid
- Slowloris (computer security)
- Virtual sit-in
- Web shell
- Radio jamming
- XML denial-of-service attack
- Xor DDoS
- Zemra
- Zombie (computing)