Cyberattack facts for kids
A cyberattack happens when someone tries to access or harm computer systems without permission. This can affect how private, correct, or available information is. Think of it like someone trying to break into your digital locker.
Today, we use computers for almost everything. This makes us more open to cyberattacks. Most computer systems have small flaws, called bugs, that bad actors can use. While no system is perfectly safe, there are many ways to protect them. This makes information security very important.
People who launch cyberattacks can be individuals, groups, or even countries. They look for weak spots in systems. Then, they use these weaknesses to create harmful software, called malware. This malware is sent to the target system. Once inside, malware can do many different things.
Sometimes, cyberattacks are hard to spot right away. Especially if the malware is trying to spy without being noticed. If an attack is found, the affected group tries to fix the problem. They also try to remove the malware and stop future attacks.
Cyberattacks can cause many problems. This includes losing money or having your personal information stolen. These attacks are usually against the rules. But it can be hard to find out who is responsible.
Contents
What is a Cyberattack?
A cyberattack is when someone tries to use computers or digital systems without permission. Their goal might be to steal, change, show, stop, or destroy information. They might also try to break into computer systems or networks.
Keeping a system safe means keeping three things secure:
- Confidentiality: This means only authorized people can see the information.
- Integrity: This means the information is correct and hasn't been changed without permission.
- Availability: This means the information and systems are always ready to be used when needed.
How Common Are Cyberattacks?
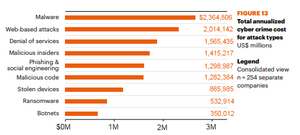
Cyberattacks happen very often. In just the first half of 2017, billions of pieces of data were stolen. Payments for ransomware attacks also reached billions of dollars.
In 2020, more people worked from home because of the COVID-19 pandemic. This led to a big increase in hacked data. Because of all these attacks, keeping information safe is a huge business worldwide. Experts predict it will be worth over $170 billion by 2022.
Why Are Systems Vulnerable?
Computers are a big part of our daily lives. They make things easier and faster. But as systems become more complex and connected, they also become more open to attacks. If an attack happens, the problems can be much bigger.
Even though software and hardware makers try their best, almost all programs have small mistakes. These are called bugs. If a bug creates a security risk, it's called a vulnerability.
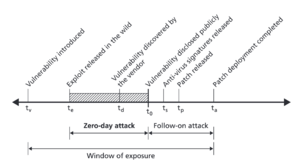
Companies often release updates to fix these known weaknesses. But some vulnerabilities are unknown, called "zero-days." These, and unpatched ones, can be used by bad actors. The best vulnerabilities let attackers put their own harmful code, or malware, onto a system. This can happen without the user even knowing. Without a weakness, attackers usually can't get into a system.
How to Stay Safe Online
How a computer system is built helps decide how safe it can be. One way to improve safety is to find weak spots and make systems stronger. But this only works partly. It's hard to know exactly how much to spend on security. This is because cyber threats are always changing.
Some experts now think that attacks will happen no matter what. So, they focus on keeping important parts working even if some areas are affected. This is called cyber resilience.
Most attacks can be stopped by keeping all your software updated. But even updated systems can still be attacked by "zero-day" weaknesses. The riskiest time is right after a weakness is found. This is because attackers can create ways to use it faster than updates can be made.
Special software helps stop unwanted access and finds harmful programs. Also, learning about online safety is key. For example, don't click on strange links or email attachments. This helps avoid attacks that rely on human mistakes.
Other ways to stay safe include:
- Keeping all private information encrypted (scrambled).
- Using strong passwords that are hard to guess.
- Installing antivirus software to stop malware.
- Making sure all your devices get regular updates.
It's impossible to make a system perfectly safe. Some strong security steps might make systems harder to use. For example, disconnecting a computer from the internet makes it very safe. But this is usually not practical for daily use.
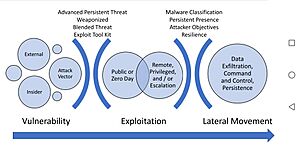
How Cyberattacks Happen
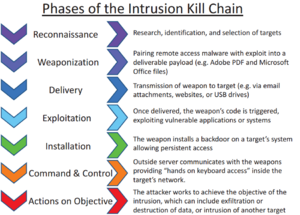
Cyberattacks often follow a series of steps. This process is sometimes called a "cyber kill chain."
- Finding Information: Bad actors first look for details about the system they want to attack. They might search for public information. Or they might use tricks to get more details from people.
- Building the Tool: After finding a weakness, attackers create a special tool. This tool, called an exploit, helps them get in. They also create malware to do what they want.
- Sending the Malware: Once ready, the malware is sent to the target. Often, this happens through phishing. This is when attackers send fake emails or messages. They try to get you to click a link or open an attachment. Sometimes, just visiting a bad website can cause a download.
- Taking Control: The attacker's software then runs on the target system. It often creates a hidden way in, called a backdoor. This lets the attacker control the system from far away.
- Staying Hidden and Acting: Many attackers don't act right away. They try to stay hidden and keep control even if the system restarts. They also try to get more power within the system. They might collect and copy data to their own devices.
What Attackers Do
Once malware is on a system, it can do many things. It depends on what the attacker wants.
- Spying: Many attackers try to secretly watch what happens on a system. This kind of malware is often hard to find.
- Taking Over Devices: Sometimes, attackers create networks of infected devices. These networks can send out lots of unwanted messages (spam). Or they can launch DDoS attacks. This floods a system with too many requests, making it crash or unusable.
- Making Money: Attackers might also use infected computers to create cryptocurrencies like Bitcoin for themselves.
- Holding Data Hostage: Ransomware is a type of malware that locks or destroys your data. Attackers then demand money to unlock it. Because of digital money like cryptocurrency, these demands have become much more common.
Who is Behind Cyberattacks?
When you think of a hacker, you might picture one person working alone. But many cyberattacks are done by skilled teams. These teams often have lots of resources. They are becoming more professional and specialized. Unlike other forms of harm, cyberattacks can be done from anywhere.
Sometimes, people inside a company or group cause attacks. They might bypass security rules to do their job faster. Attackers have different skill levels. Some are very determined to hit a certain target. Others just look for easy targets. The most skilled attackers can stay hidden in a system for a long time.
People launch cyberattacks for different reasons:
- Spying: They might want to secretly gather information.
- Changing Data: They might want to change information for their own benefit.
- Taking Control: They might want to take over systems.
- Money: Many attackers want to make money. They might sell stolen information. Or they might rent out tools that cause attacks. This is like "cybercrime for hire." It lets people without much tech skill launch attacks. For example, they might rent out a network of infected computers to send spam or launch DDoS attacks.
Who Do Cyberattacks Affect?
Cyberattacks can target anyone. This includes individuals, businesses, and even governments. Many attacks are stopped, but successful ones can cause big problems. Knowing the bad effects helps groups prepare.
Cyberattacks can cause different kinds of harm:
- Physical Harm: This can include damage to property.
- Digital Harm: Like destroying data or putting malware on systems.
- Money Problems: Such as costs from stopping operations or investigations.
- Feeling Upset: People might feel upset if their personal data is leaked.
- Bad Reputation: A company or person might lose trust after an attack.
- Wider Problems: Society might be affected if important services stop working.
Protecting Your Personal Data
Thousands of personal records are stolen every day. Most data breaches are caused by organized groups. Some are caused by people inside a company. Others are from individuals or even countries.
Bad actors often use malware or tricks to steal data. They might sell this information for money. This stolen data can include usernames, passwords, credit card numbers, or health information. This information can be used for things like sending spam or identity theft.
Impact on Important Services
Critical infrastructure includes very important services. These are things like healthcare, water, transport, and banking. These services increasingly rely on computer systems.
For a long time, people have worried about huge cyberattacks that could cause major disasters. While these extreme events haven't happened yet, smaller attacks do occur regularly. These can sometimes stop essential services for a while.
Effects on Businesses and Groups
It's hard to measure the exact money loss for businesses from cyberattacks. Some studies show small losses in stock prices. Others find no effect. Experts disagree on how much damage to reputation these attacks cause. Some think the current costs are not enough to make companies invest more in prevention.
When Governments Are Targeted
Government websites and services can also be hit by cyberattacks. Some experts think these attacks might make people trust their government less. But there isn't much proof of this yet.

What Happens After an Attack?
Responding quickly to attacks helps limit the damage. A good response needs many skills. This includes technical experts and people who can talk to the public. Because cyberattacks are so common, some companies plan their response before an attack even happens. They might have a special team ready to handle problems.
Finding the Attack
Many attacks are never found. For those that are, it takes a long time to discover them. On average, it's about 197 days. Some systems can spot unusual activity that might mean an attack. They use tools like antivirus, firewalls, or intrusion detection systems. Once something suspicious is found, investigators look for clues.
It's easier and faster to find attacks that stop systems from working. For example, a denial-of-service attack. It's harder to find attacks that secretly change or copy data. Attackers who use very valuable tools often try to stay hidden. This is so they can keep using their tools.
When an attack is found, collecting evidence starts right away. They focus on information that might disappear quickly. Gathering this data can help later if there are legal steps. But the data must be collected correctly.
Getting Systems Back Online
After an attack, a top goal is to contain the affected system. This might mean shutting it down or isolating it. They might also use a special "sandbox" system to learn more about the malware. Then, they fix the weakness and rebuild the system.
Once the exact way the system was attacked is known, usually only one or two technical fixes are needed. This helps stop the attack from happening again. A penetration test can then check if the fix works. If malware is involved, the group must find and remove all of it. They also need to close all ways the malware got in or sent data out.
Sometimes, containing an attack can make it harder to investigate. For example, shutting down servers might break agreements a company has. After the attack is fully contained, the company works to get all systems back to normal. Having backups and tested plans helps with recovery.
Rules and Consequences
Most countries agree that cyberattacks are covered by rules about using force. So, cyberattacks as a form of serious harm could be against international rules. This means those responsible could face serious consequences. There are also agreements that cyberattacks must follow rules for protecting people. If they target important civilian systems, they could be seen as very serious acts. However, it's hard for international groups to enforce these rules without knowing for sure who launched the attack.
In many countries, cyberattacks are against various laws. It's also a big challenge to prove who launched an attack in legal proceedings. In 2021, countries started talking about a new international agreement on cybercrime.
Many places have rules that require groups to tell people if their personal data has been affected by a cyberattack.
See Also
 | Valerie Thomas |
 | Frederick McKinley Jones |
 | George Edward Alcorn Jr. |
 | Thomas Mensah |