Computer virus facts for kids
A computer virus is a type of computer program that can make copies of itself. It often hides inside other programs. Just like a biological virus copies itself inside living organisms, a computer virus copies itself into other computer programs. That's how it got its name!
Besides copying itself, a computer virus can also run instructions that cause harm. This means they can affect your computer's security. Computer viruses are a type of bad software called malware.
Sometimes, people use the term "computer virus" for other kinds of malware too. This includes programs like Trojan horses and worms. Even though these are different, it can be hard to tell them apart. They often appear together, and only experts might know the exact difference. Some programs can even fit into more than one category.
Computer viruses are made for different reasons. Sometimes, they are created to spread a message or to try and change system files.
Viruses can spread in many ways. Some common ways include email, removable devices (like USB drives), and downloading files from the internet.
Contents
What Are the Main Types of Computer Viruses?
There are several different kinds of computer viruses:
- Macro viruses or script viruses are very common. These viruses are written using special script functions. These functions are often found in programs like word processors or spreadsheets.
- Boot sector viruses infect the boot sector of storage devices. This includes floppy disks, hard drives, and other media. The boot sector is a special part of the disk that helps your computer start up.
- Executable files and operating system scripts can also be infected. These are programs that run automatically. This can happen when you insert a disk or open a file.
- Cross-site scripting involves scripts on web pages. These scripts can copy themselves to other web pages.
- Any computer file can be a target. Viruses can use weaknesses like buffer overflows to spread.
How Do Computer Viruses Work?
For a computer virus to work, it needs a few key parts. It must have a way to find new files or disks to infect. It also needs a way to copy itself into those files.
Key Parts of a Virus
A typical computer virus has three main parts:
How Viruses Spread: The Infection Mechanism
The infection mechanism is how the virus spreads or moves around. It's also called the 'infection vector'. A virus usually has a search routine. This routine finds new files or disks that it can infect.
What Activates a Virus: The Trigger
The trigger is also known as a logic bomb. This is the part of the virus that decides when its harmful actions will start. It could be a specific date, a certain time, or when another program is present. It might also activate if your disk space goes over a limit. Sometimes, it just needs you to double-click a specific file.
What a Virus Does: The Payload
The "payload" is the actual part of the virus that does the damage. This is the main purpose of the virus. Sometimes, you might notice the payload working. For example, your computer might slow down or freeze. Most of the time, the payload is designed to be harmful. However, some payloads are not destructive. They might just spread false information, which is called a Virus hoax.
The Life Cycle of a Computer Virus
Just like living things, computer viruses have a life cycle. This life cycle can be divided into four main stages:
The Dormant Phase
In this stage, the virus program is just waiting. The virus has gotten onto your computer or into your software. But it isn't doing anything yet. The virus will wait for its "trigger" to activate it. This trigger could be a date, another program, or your disk filling up. It could also be you taking an action, like opening an email. Not all viruses have this waiting stage.
The Propagation Phase
This is when the virus starts to multiply. It makes copies of itself. The virus places these copies into other programs or special system areas on your disk. The copies might not be exactly the same as the original. Viruses can "morph" or change to avoid being found by anti-virus software. Each infected program will then have a copy of the virus. This copy will also start to spread.
The Triggering Phase
A virus that was dormant moves into this phase when it is activated. Now, it will perform the task it was designed for. The triggering phase can start because of different computer events. For example, it might activate after the virus has made a certain number of copies of itself.
The Execution Phase
This is the final stage where the virus does its actual work. The "payload" is released. This can be very damaging, like deleting files or crashing your computer. Or it can be less harmful, like showing funny or political messages on your screen.
How User Rights Can Stop Viruses
Older computer operating systems didn't have much access control. This meant anyone using the computer could do anything. Modern operating systems are different. They have a system for access control. There can be many users, and each user has different "privileges." Some users can only read certain files. Others might be able to change or delete files. These rules can be set for each file.
The amount of damage a virus can do depends on the rights it has. If a user doesn't have permission to write to certain parts of the system, the virus won't be able to spread there.
Sometimes, the system for managing rights is there, but it's not used by default. This happened with older systems like Windows NT or Windows XP. By default, all users had full rights, which made it easier for viruses to spread.
How Anti-Virus Software Helps
Antivirus software can help protect your computer from known viruses. Some antivirus programs scan files. They compare a special code (called a hash code) for each file with a list of known virus codes. If the codes match, it likely means a virus has been found.
However, this method has some challenges. It only protects against viruses whose codes (or "signatures") are already known. Companies that make antivirus software need to constantly update their virus lists. Then, they send these updates to your computer.
Antivirus software can scan in two ways:
- "On demand" or "manually": You choose when to scan a file or your whole computer.
- "On access": The software scans files automatically whenever your computer tries to open or use them.
Even with updates, antivirus software can't offer complete protection. Some viruses use something called polymorphic code. This means they change their signature every time they copy themselves. No matter how many signatures a company has, these types of viruses can be hard to stop.
Another way antivirus software protects you is by using heuristics. Instead of knowing every virus by its signature, heuristic software watches how programs behave. If a program does something that looks suspicious, the antivirus software can stop it. Because it has to watch every step, this method can sometimes make your computer slower.
"Live Systems" for Better Protection
One of the best ways to protect against viruses is to use a "live system." This is a system that starts up from a read-only disc, like a CD or DVD. It doesn't allow anything to be written to your hard drive or other storage devices. This makes it very hard for viruses to infect your computer.
Images for kids
-
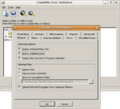
A screenshot of ClamWin, which is open-source antivirus software. It's running in Wine on Ubuntu Linux.
See also
 In Spanish: Virus informático para niños
In Spanish: Virus informático para niños