Computer worm facts for kids
A computer worm is a special kind of computer program that can copy itself and spread to other computers. It's like a digital bug that can travel across computer networks. Worms often use weaknesses in a computer's security to get inside.
Even though some worms are only made to spread, they can still cause big problems. For example, they can slow down the internet by using up too much network space, or they can cause other unexpected issues. Unlike computer viruses, which usually change or damage files, worms often focus on spreading themselves.
Contents
History of Computer Worms
The idea of a "worm" first appeared in a 1975 book called The Shockwave Rider by John Brunner. In the story, a character creates a data-collecting worm to get back at powerful people who control a huge information network. He describes it as "the biggest-ever worm loose in the net."
On November 2, 1988, a student named Robert Tappan Morris released what became known as the Morris worm. This worm caused a lot of trouble for many computers connected to the early internet. It was a big deal and led to the creation of the CERT Coordination Center, a group that helps deal with internet security problems.
What Harm Can Worms Do?
When a worm is designed to do more than just spread, the extra code is called its "payload." These payloads can be very harmful. For example, a worm might:
- Delete important files from a computer.
- Lock up your files and demand money to unlock them (this is called ransomware).
- Steal private information like documents or passwords.
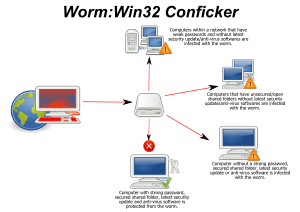
One common thing worms do is install a "backdoor" on a computer. This backdoor lets the worm's creator control the computer from far away. These controlled computers are often called "zombies." Many zombie computers linked together form a "botnet." Botnets are used for bad things, like sending out tons of unwanted emails (spam) or launching attacks that try to shut down websites (called DoS attacks).
How to Protect Your Computer from Worms
Worms often spread by finding weak spots, or "vulnerabilities," in computer operating systems. If a computer program needs you to click on something or open a file for it to spread, it's usually called a Trojan horse.
Computer companies regularly release security updates to fix these weak spots. If you install these updates on your computer, most worms won't be able to spread to it. Sometimes, a weak spot is found before a company can release a fix. This is called a "zero-day attack," and it can be very dangerous.
It's important to be careful when you get unexpected emails. You should never open attached files or programs from emails you don't trust. Also, avoid clicking on links in suspicious emails. Even with warnings, tricky emails (called phishing attacks) can sometimes fool people into running harmful code.
Using anti-virus and anti-spyware software is very helpful. Make sure to keep these programs updated often, ideally every few days. Using a firewall is also a good idea. A firewall acts like a guard for your computer, blocking unwanted connections.
Computer scientists are always looking for new ways to fight worms. One idea is to watch how many times a computer on a network tries to scan for other computers. If a computer starts scanning too much, it could mean it's infected. This lets network managers take the computer offline to check it for malware. Also, special computer learning techniques can help find new worms by studying how a suspected computer behaves.
You can help keep your computer safe by:
- Keeping your computer's operating system and other software updated.
- Being careful about opening emails you don't recognize or expect.
- Always running a firewall and antivirus software.
Images for kids
-
Morris worm source code floppy diskette at the Computer History Museum
See also
 In Spanish: Gusano informático para niños
In Spanish: Gusano informático para niños
 | Jessica Watkins |
 | Robert Henry Lawrence Jr. |
 | Mae Jemison |
 | Sian Proctor |
 | Guion Bluford |