Network Time Protocol facts for kids
 |
|
| International standard | RFC 5905 |
|---|---|
| Developed by | David L. Mills, Harlan Stenn, Network Time Foundation |
| Introduced | 1985 |
The Network Time Protocol (NTP) is a special set of rules that computers use to keep their clocks exactly in sync. Imagine all the clocks in the world needing to show the same time! NTP helps computers do this, even when they are connected through the internet, where data can sometimes travel at different speeds. NTP has been around since before 1985, making it one of the oldest internet rules still used today. It was created by David L. Mills from the University of Delaware.
NTP helps computers match their time to Coordinated Universal Time (UTC) very closely, usually within a few thousandths of a second. It uses clever methods to pick the best time sources and deal with delays in the network. Over the public internet, NTP can often keep time accurate to within a few hundredths of a second. On a local network, like at your school or home, it can be even more precise, sometimes within a thousandth of a second! NTP also warns about upcoming leap seconds, which are extra seconds added to the year to keep our clocks aligned with the Earth's rotation.
Usually, NTP works like a client–server model. This means one computer (the client) asks another computer (the server) for the correct time. But it can also work like a peer-to-peer system, where two computers share time information with each other. Computers send and receive time messages using something called User Datagram Protocol (UDP) on a specific "port" number, which is like a special address for data. NTP is currently on version 4 (NTPv4), which still works with older version 3 systems.
Contents
How Computers Sync Their Clocks
An NTP client computer regularly asks one or more NTP servers for the time. The client needs to figure out two things:
- How much its clock is different from the server's clock (the "time offset").
- How long it takes for a message to go to the server and come back (the "round-trip delay").
Imagine the client sends a message at its time `t0`. The server gets it at its time `t1`. The server then sends a reply at its time `t2`. Finally, the client gets the reply at its time `t3`. By using these four timestamps, the client can calculate how much its clock is off and how long the message took to travel.
The computer then uses these calculations to slowly adjust its own clock. It doesn't just jump to the new time, but gently speeds up or slows down its clock until it matches the correct time. This helps keep everything running smoothly.
For the most accurate time, the path that messages take to the server and back should be about the same length. If one path is much longer, it can cause small errors.
The Story of NTP
In 1979, early time synchronization technology was shown off at a big computer conference in New York. It was part of the first public demonstration of internet services working across the Atlantic Ocean using satellites! This technology later became the basis for NTP.
In 1985, the very first version of NTP (NTPv0) was created. Even with the slower computers and networks back then, it could usually keep time accurate to within a tenth of a second across the Atlantic, and even better on local networks.
Over the years, NTP kept getting better. In 1988, NTPv1 was released, which explained how client-server and peer-to-peer modes worked. NTPv2 came out in 1989, adding ways to manage the protocol and a security feature using digital signatures. NTPv3, defined in 1992, included a way to figure out all the possible errors, helping computers pick the very best time server.
The current version, NTPv4, was officially proposed in 2010. Since David L. Mills retired, a team of open-source developers now maintains the main NTP software.
Simple Network Time Protocol (SNTP)
Sometimes, the full NTP protocol was too complex for simple uses. So, in 1992, a simpler version called Simple Network Time Protocol (SNTP) was created. SNTP is easier to use because it doesn't need to store as much information over time. It's like a simpler way to get the time from just one server. SNTP still works perfectly with NTP, but because it uses simpler methods, it might not be as super-accurate.
How NTP Organizes Time Sources

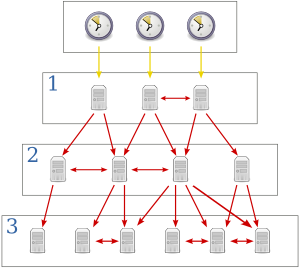
NTP uses a system of layers, called strata, to organize time sources. Think of it like a pyramid, with the most accurate clocks at the top. Each layer is given a number, starting with zero for the very best clocks. A server that gets its time from a stratum n server will be a stratum n + 1 server. This numbering helps prevent computers from getting stuck in a loop trying to sync with each other.
It's important to know that a lower stratum number doesn't always mean better quality. Sometimes, a stratum 3 time source can be more reliable than a stratum 2 one.
Here's a simple breakdown of the strata:
- Stratum 0: These are super-accurate timekeeping devices. They include atomic clocks, GPS devices, or other special radio clocks. They create a very precise signal that computers can use to set their time. These are also called reference clocks. NTP servers don't actually say they are stratum 0; a 0 in an NTP message means the stratum is not specified.
- Stratum 1: These are computers directly connected to a stratum 0 device. Their system time is almost perfectly matched to these super-accurate clocks. They are also known as primary time servers.
- Stratum 2: These are computers that get their time over a network from stratum 1 servers. A stratum 2 computer might ask several stratum 1 servers for the time to make sure it gets the most accurate reading.
- Stratum 3: These are computers that get their time from stratum 2 servers. They use similar methods to get and check time data. They can also act as servers for stratum 4 computers, and so on.
The highest stratum number is 15. If a device shows stratum 16, it means its clock is not synchronized. NTP tries to find the shortest and fastest path to the stratum 1 servers for all the computers.
NTP also uses a "reference identifier" (refid) to show where a server gets its time from. This helps prevent computers from getting into timing loops.
| Refid | Clock Source |
|---|---|
| GOES | Geostationary Operational Environmental Satellite |
| GPS | Global Positioning System |
| GAL | Galileo Positioning System |
| PPS | Generic pulse-per-second |
| IRIG | Inter-Range Instrumentation Group |
| WWVB | LF Radio WWVB Fort Collins, Colorado 60 kHz |
| DCF/PZF | LF Radio DCF77 Mainflingen, DE 77.5 kHz |
| HBG | LF Radio HBG Prangins, HB 75 kHz (stopped working) |
| MSF | LF Radio MSF Anthorn, UK 60 kHz |
| JJY | LF Radio JJY Fukushima, JP 40 kHz, Saga, JP 60 kHz |
| LORC | MF Radio Loran-C station, 100 kHz |
| TDF | MF Radio Allouis, FR 162 kHz |
| CHU | HF Radio CHU Ottawa, Ontario |
| WWV | HF Radio WWV Fort Collins, Colorado |
| WWVH | HF Radio WWVH Kauai, Hawaii |
| NIST | NIST telephone modem |
| ACTS | NIST telephone modem |
| USNO | USNO telephone modem |
| PTB | German PTB time standard telephone modem |
| MRS | (Informal) Multi Reference Sources |
| GOOG | (Unofficial) Google Refid used by Google NTP servers as time4.google.com |
For servers at stratum 2 and below, the refid is usually a coded version of the upstream server's internet address. Sometimes, the refid field can also contain special messages called "kiss-o'-death" (KoD) packets. These tell a client to stop sending requests, perhaps because the server is too busy.
Different NTP Programs
Many different programs exist that use the NTP protocol.
Main NTP Program
The main NTP program, called ntpd, has been developed for over 20 years. It's designed to work on almost any computer, from personal computers to large servers. It runs in the background to keep the clock accurate. In 2017, a check of this program found some possible security issues.
Windows Time
All versions of Microsoft Windows since Windows 2000 include a service called Windows Time (W32Time). This service can sync the computer's clock to an NTP server. It was first made to help with a security system called Kerberos, which needed clocks to be within 5 minutes of each other.
Starting with Windows Server 2003 and Windows Vista, Windows Time became more compatible with NTPv3. Microsoft used to say that W32Time couldn't keep time accurate to within one second. However, starting with Windows 10 version 1607 and Windows Server 2016, W32Time can be set up to be accurate to within 1 second, 50 milliseconds, or even 1 millisecond under certain conditions.
OpenNTPD
In 2004, a program called OpenNTPD was created. It focuses on security and is simpler than the main NTP program. While it might not be as super-accurate, it's very secure and works well for most users.
NTPsec
NTPsec is a version of the main NTP program that has been made much more secure. It was created in 2015 after some security problems were found in the original program. By removing old or unsafe features, NTPsec has a much smaller code, making it easier to check for problems.
chrony
chrony is another independent NTP program. It's known for being simpler, more secure, and using fewer computer resources. It can sync time faster and better than the main NTP program in many situations. chrony is great for regular computers that might go to sleep or have internet that cuts out sometimes. It's also good for virtual machines, which are often less stable.
chrony is considered very reliable. It can even achieve better accuracy on local networks by using special hardware in the network adapter. It also supports a new security feature called Network Time Security (NTS).
ntpd-rs
ntpd-rs is a new NTP program that focuses heavily on security. It's written in a programming language called Rust, which helps prevent certain types of errors that can lead to security problems. ntpd-rs is used in places where security is very important, like for the Let's Encrypt organization that provides website security certificates. It also supports NTS.
Leap Seconds
A leap second is an extra second added to the year to keep our clocks in sync with the Earth's slightly irregular rotation. When a leap second happens, the NTP program gets a warning. Even though the NTP clock might pause for a moment during this event, it makes sure that time still appears to move forward smoothly for all computer programs. This prevents any confusion about the order of events.
Some companies, like Google, Amazon, and Facebook, use a different method called "leap smearing." Instead of adding a full second all at once, they spread out the extra second over a 24-hour period. This makes the time change very gradual. While chrony supports this, it's not a standard NTP method, so it's usually not mixed with public NTP servers.
Keeping NTP Secure
Adjusting a computer's system time is usually a special operation that requires high permissions. Because of this, parts of NTP programs need to run with these permissions, which can sometimes create security risks. Over the years, some security problems have been found in NTP programs, but developers are always working to fix them.
For example, in 2014, a security flaw was found that could allow someone to take control of a computer running the main NTP program. Companies like Apple even used their automatic update system for the first time to fix this issue quickly. Some other NTP programs, like OpenNTPD, are designed differently to avoid such problems.
In 2017, a security check of three NTP programs found that chrony was generally more secure than the main NTP program and NTPsec.
NTP servers can also be tricked by "man-in-the-middle" attacks. This is when someone secretly intercepts and changes messages between a client and a server. If NTP messages aren't protected, an attacker could change the time on client computers. This could then cause problems for other security systems that rely on accurate time, like those used for secure websites or online payments.
NTP has also been used in "distributed denial of service" (DDoS) attacks. In these attacks, a small request is sent to an NTP server, but it's made to look like it came from the target computer. The server then sends a much larger reply to the target, flooding it with data and making it crash. To prevent this, NTP server software can be updated or set up to ignore requests from outside.
New Security Features
NTP has ways to check if servers are real. Older versions used a "symmetric key" system, but this wasn't very strong against man-in-the-middle attacks. A newer "public key" system was tried, but it also had problems and shouldn't be used anymore.
Network Time Security (NTS) is a much more secure version of NTPv4. It uses advanced encryption to make sure that time messages are safe from tampering. The great thing about NTS is that the heavy security work only needs to be done once. Even if the security server goes down, users can still get accurate time without worrying about attackers. NTS is supported by many NTP servers, including those from Cloudflare and Netnod, and can be used with chrony, NTPsec, and ntpd-rs.
Microsoft also has its own way to secure NTP messages within a Windows network, using a system called MS-SNTP.
Images for kids
See also
 In Spanish: Network Time Protocol para niños
In Spanish: Network Time Protocol para niños
 | James Van Der Zee |
 | Alma Thomas |
 | Ellis Wilson |
 | Margaret Taylor-Burroughs |