Kerberos (protocol) facts for kids
 |
|
| Developer(s) | Massachusetts Institute of Technology |
|---|---|
| Initial release | 24 January 1989 (version 4) |
| Stable release |
Version 5, Release 1.22 / 6 August 2025
|
| Written in | C |
| Operating system | Cross-platform |
| Type | Authentication protocol |
Kerberos is a special set of rules, called a protocol, that helps computers on a network prove who they are to each other. Imagine you want to log into a game or a website. Kerberos makes sure that both you and the game server know you are who you say you are. It uses "tickets" to do this.
This system was designed for a "client-server" setup. This means one computer (the client, like your laptop) talks to another computer (the server, like a game server). Kerberos makes sure both sides check each other's identity. This way, no one can pretend to be someone else. Kerberos also protects messages from being secretly listened to or replayed.
Kerberos uses a type of secret code system called symmetric-key cryptography. It needs a trusted third party, like a central security guard. It can also use public-key cryptography for some parts of the process. By default, Kerberos uses a specific internet "door" called UDP port 88.
The name Kerberos comes from Kerberos, a three-headed guard dog from Greek mythology. This dog guarded the underworld, just like the protocol guards computer networks.
Contents
History and development
The Massachusetts Institute of Technology (MIT) created Kerberos in 1988. They wanted to make their network services more secure for a project called Project Athena. The first versions, 1 through 3, were just for testing at MIT.
Kerberos version 4 was the first one released to the public. This happened on January 24, 1989. Because it used a strong encryption method called DES, the United States had rules about sending it to other countries. So, MIT made a version without the encryption, called "Bones." Other people then added the encryption back, like "eBones" from Australia.
In 1993, a new version, Kerberos 5, was released. This version aimed to fix problems and make it even more secure. It became an official standard, like a rulebook for how it should work.
In 2005, a group called the Internet Engineering Task Force (IETF) updated these rules. They added support for newer, stronger encryption methods like Advanced Encryption Standard (AES). They also made the main Kerberos 5 rulebook clearer and more detailed.
MIT still offers a free version of Kerberos. In 2007, MIT started the Kerberos Consortium. This group helps keep Kerberos updated and secure. Big companies like Oracle, Apple Inc., Google, and Microsoft are part of this group.
How the Kerberos Protocol Works
Kerberos helps computers prove who they are using a system of "tickets." Think of it like getting a ticket to a concert.
Understanding the Main Parts
- Authentication Server (AS): This is like the main ticket office. It checks your identity when you first log in.
- Ticket-Granting Service (TGS): This is like a special desk at the ticket office. Once you have your first ticket, you go here to get tickets for specific services.
- Key Distribution Center (KDC): This is the whole ticket office, including both the AS and the TGS. It's the central place for managing all the security keys and tickets.
- Ticket-Granting Ticket (TGT): This is your first ticket. You get it from the AS when you log in. It proves you are allowed to ask for other service tickets.
- Service Ticket (ST): This is a ticket for a specific service, like accessing a file server or a game. You get it from the TGS.
- Service Principal Name (SPN): This is the unique name for a service you want to use. It's like the name of the concert you want a ticket for.
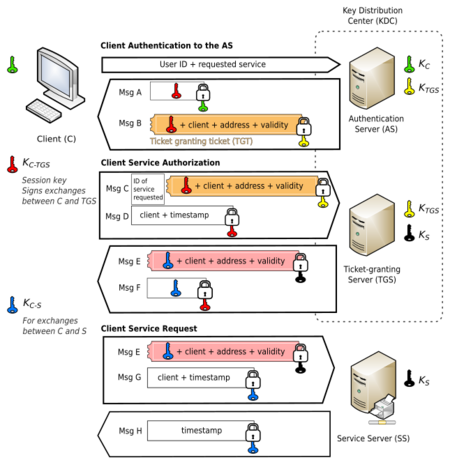
Getting Your First Ticket (Client Authentication)
1. You type your username and password into your computer. Your computer turns your password into a secret key. 2. Your computer sends your username to the Authentication Server (AS). It does NOT send your password or secret key. 3. The AS checks if your username is in its database. If it is, the AS also creates a secret key from your password. 4. The AS then sends two encrypted messages back to your computer: * Message A: This contains a special "session key" for talking to the TGS. It's encrypted with your secret key. * Message B: This is your Ticket-Granting Ticket (TGT). It's encrypted with the TGS's secret key. 5. Your computer tries to open Message A using the secret key it made from your password. If your password was correct, it can open Message A and get the "Client/TGS Session Key." This key is for talking securely with the TGS. Your computer cannot open Message B because it's for the TGS.
Getting a Service Ticket (Client Service Authorization)
1. When you want to use a specific service (like opening a shared file), your computer sends two messages to the TGS: * Message C: This includes your encrypted TGT (Message B from before) and the name of the service you want to use. * Message D: This is a special "authenticator" that proves it's really you. It's encrypted with the "Client/TGS Session Key" you got earlier. 2. The TGS receives these messages. It uses its own secret key to open your TGT (Message B). Inside, it finds your ID and the "Client/TGS Session Key." 3. Then, the TGS uses that "Client/TGS Session Key" to open Message D (your authenticator). It checks if your ID matches in both messages. 4. If everything matches, the TGS sends two new messages back to your computer: * Message E: This is your "Client-to-server ticket" for the specific service. It's encrypted with the service's secret key. * Message F: This contains a new "Client/Server Session Key" for talking to the service. It's encrypted with the "Client/TGS Session Key."
Using the Service (Client Service Request)
1. Now your computer has the tickets it needs. It connects to the Service Server (SS) and sends two messages: * Message E: The "Client-to-server ticket" you just received. * Message G: A new authenticator, encrypted with the "Client/Server Session Key." 2. The Service Server opens Message E using its own secret key. It gets the "Client/Server Session Key." 3. Then, the Service Server uses that "Client/Server Session Key" to open Message G (your authenticator). It checks if your ID matches in both messages. 4. If everything is correct, the Service Server sends a final message back to your computer: * Message H: This is a confirmation message, encrypted with the "Client/Server Session Key." 5. Your computer opens Message H. If it's correct, your computer now trusts the server, and you can start using the service!
Operating System Support
Microsoft Windows
Windows 2000 and all newer versions of Windows use Kerberos as their main way to check user identities. When a computer joins a Windows domain (a group of computers managed together), Kerberos becomes the default security system. This makes sure that when you access services within that domain, your identity is checked securely.
If computers are not part of the same trusted domain, Windows might use an older method called NTLM instead. Microsoft has also added its own changes to the Kerberos rules, which are documented for others to see.
Unix and other operating systems
Many other computer systems, like FreeBSD, Apple's macOS, Red Hat Enterprise Linux, and Solaris, also use Kerberos. Even older systems like z/OS and OpenVMS support it. This shows how widely used and important Kerberos is for computer security.
Things to Consider with Kerberos
- Time Synchronization: Kerberos needs all computers involved to have their clocks set very closely. If the clocks are off by more than a few minutes, the security checks might fail. People often use Network Time Protocol (NTP) to keep computer clocks perfectly in sync.
- Centralized Control: Kerberos relies on a central "Key Distribution Center" (KDC). If this central system is attacked, it could cause big problems.
- Service Names: Each network service often needs its own special Kerberos key. This can make setting up many different services on one computer a bit more complicated.
- Trusted Relationships: User accounts and services need to be trusted by the Kerberos system. This means setting up test environments can be tricky, as they need to be connected to the main system.
Security Aspects
Older versions of Kerberos sometimes used a weaker encryption method called Data Encryption Standard (DES). This method is no longer considered strong enough for modern security. Newer Kerberos systems use much stronger encryption, like AES, to keep your information safe. It's important for products to use these newer, more secure encryption methods.
See also
 In Spanish: Kerberos para niños
In Spanish: Kerberos para niños
- Single sign-on
- Identity management
- Generic Security Services Application Program Interface (GSS-API)