Defense in depth (computing) facts for kids
Defense in Depth is a smart way to protect computers and information. Think of it like building a super strong castle with many walls and traps! It means using lots of different security tools and methods, not just one. These tools work together in layers, like an onion, to keep important information safe from attacks. People also call it layered security or layered defense.
What is Defense in Depth?
This idea first came from the military. Soldiers would set up many lines of defense to slow down an enemy, even if they couldn't stop them right away. This gave them time to prepare and fight back.
Later, a group called the National Security Agency (NSA) started using this idea for computer security. They realized that having many layers of protection makes computer systems much harder to break into. It's like having a strong lock, an alarm system, and a guard dog all at once!
Using many layers helps to:
- Keep important information private.
- Stop bad guys from getting into critical computer systems.
- Give people time to notice and stop an attack if it starts.
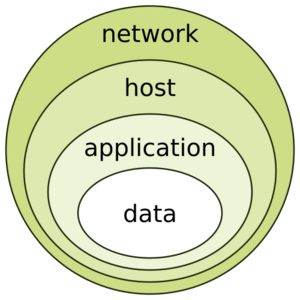
The Onion Model
Imagine an onion. It has many layers, right? The "onion model" helps us understand Defense in Depth.
- The outer layers are like the first defenses. This could be a firewall, which is like a strong gate that blocks unwanted visitors from entering your computer network.
- The middle layers are other security tools. These might be programs that check for viruses or systems that make sure only the right people can access certain files.
- The center of the onion is your most important information or data. All the layers around it work to keep it safe.
There's also a newer idea called the "kill chain." It's another military idea adapted for computers. It helps security experts understand the steps an attacker might take. By knowing these steps, they can set up defenses to stop the attack at different points along the "chain."
Ways to Use Layered Security
Here are some examples of different layers that can be used together to create strong defense:
- Antivirus software: Programs that find and remove harmful computer viruses.
- Authentication and password security: Making sure only the right people can log in, often with strong passwords.
- Biometrics: Using unique body features like fingerprints or face scans for security.
- Encryption: Scrambling information so only authorized people can read it.
- Firewall (networking): A barrier that controls what information goes in and out of a computer network.
- Hashing passwords: Turning passwords into secret codes so they are safer.
- Intrusion detection systems (IDS): Systems that watch for suspicious activity on a network.
- Logging and auditing: Keeping records of who does what on a computer system.
- Multi-factor authentication: Using more than one way to prove who you are (like a password plus a code from your phone).
- Vulnerability scanners: Tools that look for weak spots in computer systems.
- Physical security: Protecting computers and servers with real-world things like deadbolt locks on doors.
- Internet Security Awareness Training: Teaching people how to stay safe online and spot dangers.
- Virtual private network (VPN): Creating a secure, private connection over the internet.
- Sandboxing: Running risky programs in a safe, isolated area so they can't harm your main computer.
- Intrusion Protection System (IPS): Systems that not only detect but also actively stop attacks.
 | Ernest Everett Just |
 | Mary Jackson |
 | Emmett Chappelle |
 | Marie Maynard Daly |