Substitution-permutation network facts for kids
In the world of cryptography, which is about keeping information secret, an SP-network (short for substitution-permutation network) is a special way to mix up data. Think of it as a recipe for making secret codes! These networks are used in many modern block cipher algorithms, like the AES, which helps protect your online messages and data.
SP-networks work by taking a block of information (like a small chunk of a message) and transforming it step-by-step. They use two main types of steps:
- Substitution: This is like replacing letters in a secret code.
- Permutation: This is like scrambling the order of those letters.
These steps are repeated many times, making the original message very hard to guess.
Contents
How SP-Networks Work
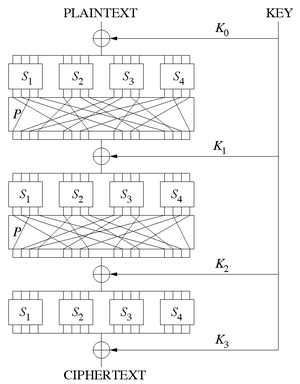
SP-networks use two main building blocks to scramble information: S-boxes and P-boxes. They work together to make sure the secret message is very well mixed.
What are S-boxes?
S-boxes, or Substitution boxes, are like mini-translators. They take a small group of input bits (bits are the smallest pieces of digital information, like 0s and 1s) and change them into a different group of output bits.
A good S-box has two important features:
- Avalanche Effect: If you change just one input bit, about half of the output bits should change. This makes it hard for someone to guess the original message by just changing a tiny part of the secret message.
- Dependence: Every output bit should depend on every input bit. This means all parts of the input contribute to all parts of the output, making the scrambling very thorough.
What are P-boxes?
P-boxes, or Permutation boxes, are like shufflers. After the S-boxes have changed the bits, the P-boxes rearrange or mix up the order of these bits. Imagine shuffling a deck of cards after changing some of them. This spreading out of bits helps to make sure that the changes from the S-boxes affect many different parts of the message.
How Keys are Used
In an SP-network, the secret key is very important. At each "round" or step of the encryption process, a part of the key (called a "round key") is combined with the data. This is usually done using a simple mathematical operation called XOR (exclusive OR). This combination with the key makes sure that only someone with the correct key can unscramble the message.
Other Ways to Encrypt
- Feistel cipher: Another common type of block cipher that works a bit differently from SP-networks.
- Product cipher: A general term for ciphers that combine two or more simple ciphers, like substitution and permutation.
- Square: A block cipher that was an early inspiration for AES.
- International Data Encryption Idea: Another strong block cipher.
 | James Van Der Zee |
 | Alma Thomas |
 | Ellis Wilson |
 | Margaret Taylor-Burroughs |