Proof of work facts for kids
Proof of work (PoW) is a clever way to prove that a computer has done a certain amount of work. Imagine it like solving a digital puzzle. One computer (the prover) solves the puzzle, and then other computers (the verifiers) can quickly check if the puzzle was solved correctly. This idea was first thought up in 1993 by Moni Naor and Cynthia Dwork. They wanted to stop bad things like denial-of-service attacks (where too many requests crash a system) or spam emails. By making computers do a little work, it becomes harder for attackers to send huge amounts of spam or overload a service.
The term "proof of work" was officially named in 1999 by Markus Jakobsson and Ari Juels. Later, PoW became very famous because of Bitcoin. Bitcoin uses PoW to make sure everyone agrees on new transactions in a network without a central boss. In Bitcoin, special computers called "miners" compete to solve these puzzles. The more computing power a miner has, the more likely they are to solve the puzzle and add new transactions to the record. PoW is one of the main ways to protect cryptocurrencies from attacks where someone tries to cheat the system.
A cool thing about proof of work is that it's asymmetrical. This means the puzzle is moderately hard to solve for the computer doing the work, but it's super easy for other computers to check the answer. This idea is also called a "CPU cost function" or "client puzzle." Many PoW systems also give rewards, usually in the form of cryptocurrency, to computers that help the network by doing this work.
The main goal of PoW isn't just to prove work was done. It's about making it very expensive and difficult for anyone to cheat or change the data. This is why PoW systems need a lot of energy and special computer parts. Because of this, some people worry about the environmental impact of PoW, especially with cryptocurrencies.
Contents
How Proof of Work Started
One of the first well-known uses of proof of work was in a system called Hashcash. Hashcash used a type of digital puzzle to prove that someone had put in effort before sending an e-mail. It was like a small "goodwill token" to show you weren't a spammer.
For example, a Hashcash message might look like this: X-Hashcash: 1:52:380119:calvin@comics.net:::9B760005E92F0DAE
To check this, a computer would do a quick calculation. It would make sure the special code (called a SHA-1 hash) of the message starts with a certain number of zeros. This check is very fast. However, finding the right code that starts with those zeros takes a lot of tries, which is the "work."
People debated if PoW systems like Hashcash could truly stop spam. The idea was to make sending lots of spam emails very costly for spammers, but still easy for regular users to send their messages. A real user shouldn't notice any delay, but a spammer trying to send millions of emails would need huge amounts of computer power. Today, PoW systems are used in more complex digital systems, like Bitcoin, which uses a similar idea to Hashcash.
Different Kinds of Proof of Work
There are two main types of proof-of-work systems:
- Challenge–response: In this type, two computers talk directly. One computer (the "server") gives a puzzle (a "challenge") to the other computer (the "client"). The client solves the puzzle and sends the answer back. The server then checks the answer. Since the server creates the puzzle on the spot, it can make it harder or easier depending on how busy it is.
- Solution–verification: This type doesn't need computers to talk directly. The computer doing the work (the "requester") creates its own puzzle and solves it. Then, it sends both the puzzle and the solution to the other computer (the "provider"). The provider then checks both the puzzle and the solution. Most systems like Hashcash work this way.
The way these puzzles work can also depend on what part of the computer they use the most:
- CPU-bound: These puzzles rely on the speed of the computer's main processor (CPU). Since CPUs get faster over time, the difficulty of these puzzles can change a lot.
- Memory-bound: These puzzles depend on how fast a computer can access its memory. This type of puzzle is less affected by how fast processors get.
- Network-bound: Here, the computer doesn't do much computing itself. Instead, it has to collect special "tokens" from other computers over the internet before it can get the final service. The "work" here is mostly waiting for information to travel across the network.
Some PoW systems also have a shortcut feature. This allows someone who knows a secret (like a private key) to create PoWs very cheaply. This might be useful for things like sending out a newsletter to many people without a high cost.
Examples of Proof-of-Work Functions
Here are some examples of the types of puzzles used in proof-of-work systems:
- Partial hash inversion (like in Hashcash)
- Hash sequences
- Puzzles
- Diffie-Hellman–based puzzles
- Cuckoo Cycle
- Merkle tree–based puzzles
Proof of Useful Work (PoUW)
Some researchers are working on a new idea called "proof of useful work" (PoUW). Instead of computers solving puzzles that don't have any other purpose, PoUW aims to make the work useful. For example, in a system called Ofelimos, the computers that help secure the network also work together to solve complex math problems. This means the energy used for PoW isn't just for security; it's also helping to solve real-world problems at the same time.
Bitcoin's Proof of Work System
In 2009, the Bitcoin network started. Bitcoin is a digital currency that uses a proof-of-work system similar to Hashcash. But in Bitcoin, PoW helps prevent "double-spending," which is when someone tries to spend the same digital money twice. Bitcoin is very secure because its protection comes from all the computing power used by its network.
New Bitcoins are "mined" by individual computers using the Hashcash-like PoW puzzle. Other computers in the Bitcoin network then check and confirm this work. The difficulty of these puzzles is regularly changed to make sure new blocks of transactions are added to the Bitcoin record (called the blockchain) at a steady pace.
Energy Use in Bitcoin
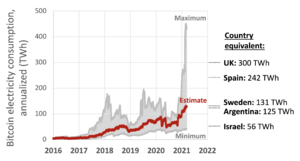
Since Bitcoin became popular, proof of work has been the main way to design peer-to-peer cryptocurrencies. However, PoW needs a huge amount of computing power, which uses a lot of electricity. Studies in 2018 from the University of Cambridge suggested that Bitcoin's energy use was similar to that of an entire country like Switzerland. This high energy use is a big concern for environmentalists.
Protecting Bitcoin History
When a new block of transactions is added to the blockchain, it's like a confirmation of those transactions. The more blocks that are added after your transaction, the harder it is for anyone to change that transaction in the blockchain. This is why businesses often wait for a few "confirmations" before they accept a Bitcoin payment as final. It would take an attacker controlling more than half of the network's total computing power to successfully change past transactions. This kind of attack is called a 51% attack.
Specialized Mining Hardware
Within the Bitcoin community, many miners join together in mining pools to combine their computing power. Some miners also use special computer chips called application-specific integrated circuits (ASICs). These ASICs are designed only for mining and are much more efficient than regular computers. This trend towards mining pools and ASICs has made it very hard for most people to mine some cryptocurrencies profitably without special equipment or access to cheap electricity.
Some PoW systems try to be "ASIC-resistant." This means they try to limit how much better an ASIC can be compared to a regular computer graphics card (GPU). The goal is to keep mining possible for more people using common hardware. However, this also means it might be easier for an attacker to rent a lot of regular computing power to launch a 51% attack against a cryptocurrency.
Environmental Concerns
The process of Bitcoin-style mining is very energy-intensive. This is because the proof-of-work system works like a lottery. Miners have to try many solutions until one of them gets the right answer. The computing work itself doesn't have any other use; it's just to secure the network. Miners use a lot of energy to add new blocks of transactions to the blockchain. They also need to buy and house large amounts of computer hardware, which adds to the cost and environmental impact.
Because of these concerns, some officials have called for changes. In January 2022, Erik Thedéen, a leader at the European Securities and Markets Authority, suggested that the European Union should consider banning the proof-of-work model. He believes the proof of stake model, which uses much less energy, would be better.
In November 2022, the state of New York put a two-year pause on new cryptocurrency mining operations that don't use 100% renewable energy. Existing mining companies that don't use renewable energy can continue, but they can't expand or renew their permits. This shows a growing effort to address the environmental impact of PoW mining.
See also
 In Spanish: Sistema de prueba de trabajo para niños
In Spanish: Sistema de prueba de trabajo para niños
- Bitcoin
- Cryptocurrency
- Proof of stake
- Consensus (computer science)