Symmetric-key algorithm facts for kids
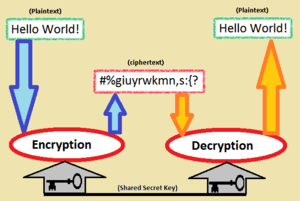
Symmetric-key algorithms are a way to send secret messages. They are part of cryptography, which is the study of secure communication. Imagine you have a secret code. With symmetric-key algorithms, the same secret code, or "key," is used to both scramble (encrypt) a message and unscramble (decrypt) it.
This secret key must be known by everyone who wants to send or receive messages. It can be made randomly, from a password, or shared using special methods like Diffie-Hellman key exchange.
Symmetric-key algorithms are very important because they are super fast for computers to use. There's another type called public-key cryptography (or asymmetric-key algorithms). With public-key methods, you use one key to encrypt a message and a different key to decrypt it. The encryption key can be shared with anyone. This is useful, but public-key methods are much slower. So, usually, public-key methods are only used to share the secret symmetric key. Then, the faster symmetric-key algorithms do all the heavy work of encrypting the actual messages.
There are two main types of symmetric-key algorithms: stream ciphers and block ciphers. Stream ciphers encrypt a message bit by bit, like a continuous flow. Block ciphers take chunks of data, called "blocks," and encrypt them all at once. Older block ciphers often used 64-bit blocks. Modern ones, like the Advanced Encryption Standard (AES), use larger 128-bit blocks.
Some popular symmetric ciphers you might hear about include Twofish, Serpent, AES, Blowfish, CAST5, RC4, TDES, and IDEA.
In the past, some secret code-breaking methods used the idea of "symmetry" to find weaknesses in these systems. These attacks are called things like known-plaintext attacks or chosen plaintext attacks.
Other names for symmetric-key encryption are secret-key, single-key, shared-key, or one-key encryption. Sometimes it's also called private-key encryption, but this can be confusing because "private key" means something different in public-key cryptography.
Contents
Symmetric vs. Asymmetric Keys
Let's look at how symmetric and asymmetric key algorithms are different. Unlike symmetric algorithms, asymmetric key algorithms use two different keys. One key is for encrypting messages, and the other is for decrypting them. This means someone can encrypt a message for you, but they can't decrypt it themselves.
How Fast Are They?
Symmetric-key algorithms are much faster for computers to process than asymmetric-key algorithms. Asymmetric methods can be hundreds or even thousands of times slower! This is why symmetric keys are used for most of the actual message encryption.
Managing Secret Keys
One challenge with symmetric-key algorithms is that everyone needs to have the exact same secret key. If you have a group of people, say n people, and everyone needs to talk secretly with everyone else, you would need many keys. The number of keys needed is calculated as n times (n minus 1) divided by 2. This can become a lot of keys to manage!
Also, these keys should be changed often to keep them safe. They also need to be kept secret when they are shared and while they are being used. The whole process of choosing, sharing, and storing these keys is called key management. It can be tricky to do this safely and reliably.
Combining Both Methods
In today's secure systems, both asymmetric (public key) and symmetric algorithms are often used together. This is called a hybrid cryptosystem. They combine the best parts of each method.
Asymmetric algorithms are used first to safely share the symmetric key at the start of a communication session. Once everyone has the symmetric key, the faster symmetric-key algorithms can be used to encrypt all the messages that follow. This makes sharing keys much easier. Asymmetric keys only need to be shared in a way that proves they are real (authentic). Symmetric keys need to be shared both authentically and secretly.
Some examples of systems that use this combined approach include SSL (which you might see in website addresses as HTTPS), PGP, and GPG.
Related Topics
See also
In Spanish: Criptografía simétrica para niños
 | Claudette Colvin |
 | Myrlie Evers-Williams |
 | Alberta Odell Jones |