Computer security facts for kids
Computer security is all about keeping computers, phones, and online information safe. It's also called cybersecurity or digital security. Think of it as protecting your digital world from bad things. This includes keeping your computer software, systems, and networks safe.
The goal is to stop people from getting your private information without permission. It also prevents them from stealing or damaging your computer parts, software, or data. Computer security also makes sure that the online services you use work correctly.
Why is this so important? We use computer systems for almost everything today! From the Internet to smartphones and smart devices like televisions. Even everyday items connected to the internet, called the Internet of things (IoT), need protection. Cybersecurity is a big challenge because our digital world is growing fast. It's super important for systems that control big things like power grids and finance.
While many security steps are digital, like passwords and encryption, some are physical. For example, a metal lock on a computer can stop someone from messing with it.
Contents
- Understanding Cyber Threats
- Secret Backdoors
- Stopping Services: DoS Attacks
- Physical Computer Attacks
- Digital Eavesdropping
- Harmful Software: Malware
- Man-in-the-Middle Attacks
- Smart, Changing Attacks
- Tricky Phishing Scams
- Gaining More Access: Privilege Escalation
- Hidden Clues: Side-Channel Attacks
- Tricking People: Social Engineering
- Pretending to Be Someone Else: Spoofing
- Changing Things: Tampering
- Hidden Code: HTML Smuggling
- Keeping Your Information Safe
- How to Protect Your Devices
- Systems That Need Protection
- Protecting Money and Banking
- Keeping Essential Services Safe
- Air Travel Security
- Protecting Your Gadgets
- Healthcare Systems
- Big Companies and Their Data
- Cars and Cyber Safety
- Tracking Goods Safely
- Government and Public Systems
- Smart Devices and Physical Risks
- Medical Equipment Safety
- Power Grid Security
- Phone and Communication Safety
- What Cyber Attacks Cost
- Why Do People Attack Computers?
- Dealing with Cyber Attacks
- Famous Cyber Attacks
- Government's Role in Cybersecurity
- Working Together Globally
- Cyber Warfare
- Careers in Cybersecurity
- Key Cybersecurity Terms
- A Brief History of Cybersecurity
- See also
- See also
Understanding Cyber Threats
A vulnerability is like a weak spot in a computer or system. It's a flaw that can let someone get past its security. Many known weaknesses are listed in a big database called Common Vulnerabilities and Exposures (CVE). If a weakness can be used to cause harm, it's called an exploitable vulnerability. People who try to find and use these weaknesses are called threats or attackers.
Anyone can be a target of cyber attacks. But different groups might face different kinds of attacks. For example, in 2023, a UK report showed that about 32% of businesses and 24% of charities had been attacked. Larger organizations were hit more often. However, smaller businesses are also at risk because they might not have strong security tools. They often face malware, ransomware, phishing, and Denial-of-Service (DoS) attacks.
Regular internet users are often targeted by attacks that try to hit as many devices as possible. These attacks use common internet methods like phishing, ransomware, and scanning. To keep your computer safe, it helps to know about these different types of attacks.
Secret Backdoors
A backdoor is a secret way to get into a computer system. It lets someone bypass normal security checks, like passwords. These secret ways can be part of the original design or happen because of mistakes in setting up a system. Backdoors are a bigger worry for companies and large databases than for individual users.
Sometimes, a backdoor is put there on purpose by someone allowed to access the system. But attackers can also add them for bad reasons. Bad actors often use malware to put backdoors on computers. This gives them control from far away. With this access, they can change files, steal private information, or even take over the whole computer. Backdoors are hard to find because they are often hidden deep inside the computer's programs.
Stopping Services: DoS Attacks
A Denial-of-Service (DoS) attack tries to make a computer or website unusable for its normal users. Imagine too many people trying to enter a door at once, blocking everyone. Attackers might try to lock you out of your account by typing the wrong password many times. Or they might flood a website with so much traffic that it crashes.
If an attack comes from one place, it's easier to block. But many DoS attacks are distributed (DDoS). This means the attack comes from many different computers at once. These attacks are much harder to stop. They can use zombie computers, which are computers secretly controlled by attackers. Attackers do this to cause problems or make a statement.
Physical Computer Attacks
A physical access attack happens when someone unauthorized gets their hands on your computer. They might want to copy your data or steal information directly. Attackers could also change your computer's settings or install harmful programs. These programs could be worms, keyloggers (which record what you type), or hidden listening devices.
Even if your computer has passwords, an attacker with physical access might bypass them. They could start the computer using a special CD-ROM or USB drive. Tools like Disk encryption (which scrambles your data) help protect against these attacks. Some attacks also target a computer's memory directly, using special features of modern computers.
Digital Eavesdropping
Eavesdropping means secretly listening in on private digital conversations. This often happens when you use an unsecured Wi-Fi network. If your data isn't encrypted, an attacker can intercept it. Imagine sending a secret note, but someone is reading it over your shoulder.
Unlike other attacks, eavesdropping usually doesn't slow down your device. This makes it hard to notice. An attacker might put special software on a device. Later, they can collect any information that software found.
To protect yourself, use a virtual private network (VPN). A VPN encrypts your data, making it unreadable to others. Always use HTTPS (secure websites) instead of just HTTP. Also, make sure your home Wi-Fi network uses strong encryption. Even computers not connected to the internet can be listened to by picking up tiny electronic signals they give off.
Harmful Software: Malware
Malware is short for "malicious software." It's any computer program made to harm your computer or you. If malware gets on your device, it can steal private information like passwords. It can also give attackers control of your computer. Sometimes, it can even damage or delete your files forever.
Different Kinds of Malware
- Viruses are like biological viruses. They attach to programs and spread copies of themselves to other programs. They need you to run the infected program to work.
- Worms are similar to viruses but can spread on their own. They don't need you to open a program to move between devices.
- Trojan horses pretend to be useful programs. They trick you into installing them. Once installed, they can create a secret way for attackers to control your device.
- Spyware secretly collects information from your computer. It sends this private data back to the attacker. A common type is a keylogger, which records everything you type. This can steal usernames, passwords, and credit card numbers.
- Scareware tries to scare you into buying or installing unwanted software. You might see a pop-up warning you about a fake virus or a legal problem. It uses tricks to make you feel worried.
- Ransomware locks your files and demands money to unlock them. It encrypts your data, making it unreadable. Attackers usually ask for payment in digital currency like Bitcoin.
Man-in-the-Middle Attacks
A Man-in-the-Middle (MITM) attack is when an attacker secretly gets between two people or systems communicating. They pretend to be one of the parties to listen in or change messages. Imagine you're talking to a friend, but someone else is secretly relaying your messages and changing them.
Here are some ways MITM attacks happen:
- IP address spoofing: The attacker pretends to have a different internet address to redirect your online traffic.
- Message spoofing: Attackers send fake emails or texts that look like they're from someone you trust. They can then read your messages or trick you.
- Wi-Fi spoofing: An attacker sets up a fake Wi-Fi hotspot. If you connect to it, they can see and change your internet traffic.
- DNS spoofing: This tricks your computer into thinking a fake website is real. When you try to visit a site, you're sent to the attacker's fake version instead.
- SSL hijacking: This attack tries to break the secure connection (like when you see "HTTPS") between your browser and a website. This lets the attacker see your encrypted information.
Smart, Changing Attacks
Since 2017, a new kind of attack has appeared: multi-vector, polymorphic attacks. These attacks are very clever. They combine several types of attacks at once. They also change their form as they spread. This makes them very hard for security systems to detect.
"Multi-vector" means they use many ways to spread, like through websites, emails, and apps. "Polymorphic" means they constantly "morph" or change their code. This makes it almost impossible for older security tools to recognize them.
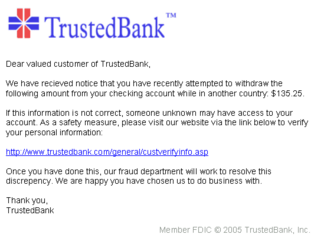
Tricky Phishing Scams
Phishing is when attackers try to trick you into giving them private information. This includes usernames, passwords, or credit card numbers. They do this by pretending to be someone you trust. Phishing often happens through fake emails, text messages, or phone calls.
These scams often send you to a fake website. The fake site looks almost exactly like a real one. It asks for your personal details, like your login and password. Once you enter them, the attackers can use that information to get into your real accounts.
Phishing is a type of social engineering. This means they use tricks to get your trust. A common trick is sending fake bills for things you didn't buy. They tell you to click a link if the purchase wasn't yours. A more targeted type is spear-phishing. This attack focuses on specific people. It uses personal details to make the scam seem more real.
Gaining More Access: Privilege Escalation
Privilege escalation is when an attacker who has limited access to a system manages to get more access. Imagine someone who can only open one door, but then finds a way to get a master key. For example, a regular computer user might find a weakness to get into secret data. They might even become a "superuser" with full control.
These attacks can start with social engineering tricks, like phishing. There are two main types:
- Horizontal escalation: An attacker gets into a regular user's account. They might steal a username and password. From there, they can move around the network, accessing other information at the same low level.
- Vertical escalation: This targets people with more power, like an IT administrator. If an attacker gets their high-level account, they can then get into many other accounts.
Hidden Clues: Side-Channel Attacks
A Side-channel attack uses hidden clues that a computer system gives off. Every computer affects its surroundings in some way. This could be tiny amounts of heat, sound, or even electromagnetic signals. Attackers gather these small pieces of information. They use them to guess what's happening inside the system. This can help them get information that is supposed to be secret. These clues are often very hard to detect because they are so faint.
Tricking People: Social Engineering
Social engineering is about tricking people to get secret information. Attackers might pretend to be someone important, like a bank official or a boss. They try to get you to reveal passwords or give them access. They play on your trust and how your brain usually works.
A common trick is sending fake emails that look like they're from your CEO. These emails might ask you to do something urgent. Phishing attacks are a main type of social engineering. These scams have cost businesses a lot of money. For example, a sports team once had employee tax forms stolen because someone pretended to be their president.
Pretending to Be Someone Else: Spoofing
Spoofing is when someone pretends to be a trusted person or system. They do this by faking data, like an email address or an internet address. Their goal is to get information or access they shouldn't have. Spoofing is very similar to phishing.
Here are some types of spoofing:
- Email spoofing: An attacker fakes the sender's address on an email. It looks like it came from someone else.
- IP address spoofing: An attacker changes their internet address. This hides who they are or makes them look like another computer.
- MAC spoofing: An attacker changes the unique address of their network device. This hides their identity or lets them pretend to be another device.
- Biometric spoofing: An attacker creates a fake fingerprint or face scan. They use it to pretend to be another person.
- ARP spoofing: This tricks devices on a local network. It makes them send data to the attacker instead of the right computer.
Changing Things: Tampering
Tampering means changing data or a system without permission. It's a harmful act that changes how a system works or what its data says. For example, someone might secretly change a computer's settings. Or they might put hidden surveillance tools into network devices.
Hidden Code: HTML Smuggling
HTML smuggling is a trick where attackers hide harmful code inside a web page. These HTML files look harmless. They can sneak past security filters. Once you open the web page, your browser "decodes" the hidden script. This then releases malware onto your device.
Keeping Your Information Safe
How people act can greatly affect information security. This is true for big companies and for you at home. It's about building good habits to protect information. Studies show that many security problems happen because of human error.
Improving security is an ongoing process. It's like a cycle of checking and making changes. To keep information safe, everyone needs to be aware and follow good practices.
How to Protect Your Devices
A countermeasure is anything that helps protect your computer. It can be an action, a device, or a method. Countermeasures reduce threats and weaknesses. They work by stopping attacks, making them less harmful, or helping to find them.
Here are some common ways to protect your computers and data:
Security Built-In
Security by design means that software and systems are built to be safe from the very beginning. Security isn't an afterthought; it's a main part of the plan.
Here are some ideas behind building secure systems:
- Least Privilege: Each part of a system only gets the access it absolutely needs. If an attacker gets into one part, they can't easily access everything else.
- Defense in Depth: This is like having many layers of security. An attacker would need to get past several defenses to cause real harm.
- Safe Defaults: Systems should be set up to be secure by default. It should take a clear choice to make them less secure.
- Tracking Activity: Systems keep records of what happens. These audit trails help figure out how an attack happened.
- Openness about Weaknesses: When security flaws are found, it's important to share them. This helps fix them quickly.
Planning for Security
Security architecture is about planning how computer systems are put together to be safe. It's like an architect designing a building to be strong and secure. The goal is to make it hard for attackers to get in. It also aims to limit the damage if an attack does happen. A security architect makes sure that all parts of a system work together to keep it secure. They also check that new changes are safe.
Common Security Tools
Good computer security involves three steps: stopping threats, finding them, and reacting to them. Here are some ways this is done:
- Limiting Access: Only allow certain people to use specific parts of a system. This is done with user accounts and access controls.
- Firewalls: These are like guards for your network. They check all incoming and outgoing internet traffic. They block anything that looks suspicious. Firewalls can be software on your computer or separate hardware devices.
- Intrusion Detection Systems (IDS): These tools watch for attacks happening right now. They help figure out what happened after an attack.
- Responding to Attacks: If an attack happens, you need a plan. This could be updating your security or telling the authorities. Sometimes, a damaged system might need to be completely rebuilt.
- Cybersecurity Training: Learning about cyber threats helps people avoid them.
- Web Proxies: These can stop you from visiting bad websites. They check content before it reaches your computer.
The main goal of security is to protect the CIA triad:
- Confidentiality: Keeping information secret from unauthorized people.
- Integrity: Making sure data is accurate and hasn't been changed.
- Availability: Ensuring that systems and data are always ready for use.
Finding and Fixing Weaknesses
Vulnerability management is about finding and fixing weak spots in software and systems. It's a key part of keeping computers and networks safe.
Special tools called vulnerability scanners look for known weaknesses. They check for things like open network connections or bad software settings. These tools need to be updated often to find the newest problems. Sometimes, experts are hired to do penetration tests. They try to hack into a system to find its weaknesses before real attackers do.
Making Systems Stronger
To make systems safer, we look for risks and test for weaknesses. You can lower the chance of an attack by keeping your software updated. These updates often include security patches that fix problems.
No security measure can stop every attack. But good steps can lessen the damage. Always make backups of your important files. This way, if data is lost, you can get it back.
One great way to boost security is two-factor authentication. This means you need two things to log in. It's usually something you know (like a password) and something you have (like your phone). This makes it much harder for someone else to get into your accounts.
Protecting against physical attacks and social engineering is also key. This often involves training people. Learning about tricks and threats helps everyone stay safer online.
Hardware Security
Besides software, computer hardware can also help with security. These methods often need physical access to be bypassed, making them stronger.
- USB Dongles: These small devices plug into a USB port. They can act like a key to unlock software or a computer. They create a secure connection that's hard to copy.
- Trusted Platform Modules (TPMs): These are special chips inside computers. They add strong encryption features. They help make sure only authorized devices can connect to a network.
- Case Intrusion Detection: Some computer cases have sensors. They can tell if someone opens the computer. The computer will then show a warning when it starts up.
- Drive Locks: These are software tools that encrypt your hard drives. This makes your data unreadable if someone steals your computer.
- Disabling USB Ports: Turning off USB ports can stop people from plugging in infected devices.
- Turning off Unused Devices: Disconnect or disable cameras, GPS, or other devices you're not using.
- Mobile Access: Your phone can be used for security too. Features like Bluetooth, NFC, and fingerprint readers can help you access systems securely.
Safe Operating Systems
A secure operating system is one that has been checked by security experts. These systems are built to be very safe. Using them is a good way to improve your computer's security. They often get special certifications, like Common Criteria (CC), to show they meet high security standards.
Writing Safe Code
Secure coding is about writing computer programs in a way that avoids security weaknesses. It's part of building software that is secure by design. The goal is to prevent mistakes that could lead to security problems. This is very important for programs that handle sensitive information.
Controlling Access
Computer systems use different ways to control who can do what. Two common methods are:
- Access Control Lists (ACLs): These are like lists of permissions. For example, a file might have an ACL that says who can read it, write to it, or delete it.
- Role-Based Access Control (RBAC): This gives access based on a person's job or "role." For example, all students might have one set of permissions, while teachers have another. This makes managing access easier in large organizations.
Learning to Be Safe Online
You, the user, are a very important part of computer security. Many security problems happen because of human mistakes. These include using weak passwords or sending private emails to the wrong person. Not being able to spot fake websites or dangerous email attachments is also a risk. For example, saving your passwords in your web browser can make it easy for attackers if they get into your computer. Using two-factor authentication helps a lot with this.
Learning about online safety is very important. It helps protect you and others from many cyber threats. When everyone knows how to be safe, it creates a stronger defense against attacks.
Good Digital Habits: Cyber Hygiene
Digital hygiene or cyber hygiene is like personal hygiene for your digital life. It means doing simple, routine things to stay safe online. Good cyber hygiene adds another layer of protection. It helps stop common cyberattacks.
Common digital hygiene habits include:
- Keeping your anti-malware software updated.
- Making cloud back-ups of your important files.
- Using strong, unique passwords.
- Making sure you have limited "admin" rights on your computer.
- Using network firewalls.
These are simple steps that anyone can do. They don't need special tech skills. Just like washing your hands keeps you healthy, good cyber hygiene keeps your digital life safe.
Why Attacks Are Hard to Stop
Dealing with security breaches can be very tough. Here's why:
- Finding Attackers: It's hard to know who is attacking. They often hide their tracks using special tools or by being in another country. If they get in, they might delete their digital footprints.
- Too Many Attacks: There are so many attacks happening all the time. Many are from automated tools. It's impossible to chase after every single one.
- Law Enforcement Challenges: Sometimes, police might not have the skills or resources to track down cyber attackers. Finding attackers can involve looking at data from many places and countries.
Types of Security Tools
Here are some common types of security and privacy tools:
- Access control: Controls who can use what.
- Anti-malware: Software that fights harmful programs.
- Antivirus software: Helps protect against computer viruses.
- Cryptographic software: Uses codes to protect information.
- Data loss prevention software: Stops private data from leaving your system.
- Firewall: Blocks unwanted network traffic.
- Intrusion Detection System (IDS): Finds suspicious activity.
- Parental control: Helps parents manage kids' online access.
- Sandbox: A safe, isolated space to run programs.
- Software and operating system updating: Keeping your software current.
- Vulnerability Management: Finding and fixing weaknesses.
Systems That Need Protection
More and more computer systems are being used by everyone. This means more systems are at risk of cyberattacks.
Protecting Money and Banking
Financial systems are big targets for cybercriminals. This includes banks and places that handle credit card numbers. Attackers want to steal money or sell private information. Even in-store payment systems and ATMs can be tampered with.
People are often worried about their credit card security online. Technologies like SSL and TLS help keep your online payments safe. They encrypt your information when you shop or bank online. Credit card companies have also developed secure chips for cards to make them safer.
Keeping Essential Services Safe
Computers control many important services we use every day. This includes telecommunications, the power grid, and water systems. If these systems are connected to the internet, they can be attacked. Even systems not connected to the internet can be at risk. For example, the Stuxnet worm showed that even isolated industrial equipment can be harmed.
Air Travel Security
The aviation industry relies on many complex computer systems. A power outage at one airport can affect flights worldwide. Air traffic control and aircraft systems could be attacked. This could lead to big problems, like planes getting lost or even crashes.
Making airplanes more secure is tricky because of weight limits. Adding heavy security devices could reduce how many passengers or how much cargo a plane can carry. Modern passports now have microchips with your photo and information. This helps prevent identity fraud. Airlines also use e-tickets for easier travel.
Protecting Your Gadgets
Your everyday devices are often targets for attackers. This includes desktop computers, laptops, smartphones, tablet computers, and smart watches. Attackers want to steal passwords or financial details. They might also try to use your device to attack others.
Many of your mobile devices have cameras, microphones, and GPS. These sensors could be used by attackers to collect your private information. Even smart home devices, like smart thermostats, can be targets. Attackers could use Wi-Fi or Bluetooth to get into your devices. They might even turn on your sensors remotely.
Healthcare Systems
Many healthcare providers use the internet for services like tele-health. Patient records are also stored on computer networks. This makes healthcare more efficient. However, these systems hold very private health information. This makes them attractive targets for attackers. Hospitals have faced ransomware attacks and data breaches.
Big Companies and Their Data
Large companies are often targets for cyberattacks. Attackers often want to steal money through identity theft. This leads to data breaches, where millions of customer details are stolen. Companies like Target Corporation and Home Depot have experienced this.
Sometimes, attacks are not about money. For example, Sony Pictures was hacked. The goal was to embarrass the company and damage their computers.
Cars and Cyber Safety
Cars today are like computers on wheels. They have many computer systems for things like cruise control and airbags. Connected cars use Wi-Fi and Bluetooth. Self-driving cars will be even more complex. All these systems have security risks.
A harmful CD could be used to attack a car. Or a car's microphone could be used for eavesdropping. If attackers get into a car's main computer system, the danger is much bigger. In one test, hackers took control of a car from far away. Car makers are now sending security updates to cars over the air.
Tracking Goods Safely
Shipping companies use RFID (Radio Frequency Identification) technology. This helps them track packages. RFID tags can be read from a distance. This makes tracking goods more efficient and secure. Companies like FedEx and UPS use RFID.
Government and Public Systems
Government and military computer systems are often attacked. These attacks can come from activists or other countries. They might target things like traffic light controls or police communications. Even student records can be at risk.
Important government buildings use secure access technology. This helps control who can enter. More and more companies are also using these digital security systems for their buildings.
Smart Devices and Physical Risks
The Internet of things (IoT) is a network of everyday objects connected to the internet. This includes devices, cars, and even buildings. They have sensors and software that let them collect and share data. But there are worries that these devices are being made without enough thought for security.
IoT devices connect the digital world to the physical world. This creates new risks. If your front door lock is connected to the internet, a hacker could unlock it from a stolen phone. In a world with many IoT devices, you could lose more than just your credit card numbers. Attacks that affect physical things or people's lives are called cyber-kinetic attacks. As more IoT devices are used, these attacks could become more common and dangerous.
Medical Equipment Safety
Medical devices can also be targets for attacks. This includes hospital equipment and devices inside the body, like pacemakers. Hospitals have been hit by ransomware and other attacks. These attacks can steal sensitive patient data. It's important for makers of medical devices to keep them secure.
Power Grid Security
The energy sector, like power grids, faces real cyberattack risks. An attack could cause a long power outage in a large area. This could be as bad as a natural disaster. As energy systems become more connected, there are more places for attackers to try and get in.
Phone and Communication Safety
Your phone's SIM card is a key part of its security. It helps keep your phone service safe. New technologies are being developed to make mobile payments and other phone features even more secure. This includes ways to send payment information safely "over-the-air."
What Cyber Attacks Cost
Security breaches can cause a lot of financial damage. It's hard to know the exact cost of every attack. But experts estimate that cyberattacks cost billions of dollars each year. These costs can come from fixing damaged systems or dealing with stolen data. Companies try to spend the right amount on security. They want to protect their information without spending too much.
Why Do People Attack Computers?
People attack computer systems for many different reasons.
- Fun or Vandalism: Some attackers do it just for the thrill or to cause trouble.
- Activists: Some are "hacktivists" who attack companies they disagree with. They might try to crash a website to get attention.
- Money: Many attackers are criminals. They want to steal money or valuable information.
- Governments: Some attacks are done by governments. They might want to spy or cause problems for other countries. For example, the 2015 Ukraine power grid hack was a serious attack on a country's power system.
Understanding why people attack helps us protect systems better. A home computer needs different protection than a bank or a military network.
Dealing with Cyber Attacks
Computer security incident management is how organizations handle cyberattacks. The goal is to stop an attack quickly and limit the damage. If an attack isn't found and stopped fast, it can lead to bigger problems.
Having a plan helps. This plan tells everyone what to do during an attack. It helps them find the problem, stop it, and get things back to normal.
The main steps are:
- Prepare: Get ready for possible attacks.
- Detect and Analyze: Find out if an attack is happening and what it is.
- Contain and Recover: Stop the attack from spreading. Remove the bad software. Get systems and data working again.
- Learn: After an attack, figure out how it happened. Use this to improve future security.
Famous Cyber Attacks
Here are some examples of well-known computer security breaches:
The First Internet Worm
In 1988, there were about 60,000 computers on the internet. On November 2, 1988, many of them started to slow down. This was because of a harmful program that used up their processing power. It was the first internet computer worm. This worm spread itself to other computers. It was created by a student named Robert Tappan Morris. He said he just wanted to count how many computers were online.
Attack on Rome Laboratory
In 1994, unknown attackers broke into the Rome Laboratory. This was a main research center for the US Air Force. They used Trojan horses to get full access to the computer systems. The attackers stole secret files. They also used their access to get into other connected networks. These included systems at NASA and other defense companies.
TJX Credit Card Theft
In 2007, the company TJX announced a big computer security breach. Attackers got into their systems without permission. They stole data from millions of credit cards, debit cards, and other customer information.
The Stuxnet Attack
In 2010, a computer worm called Stuxnet caused major damage. It reportedly ruined many of Iran's nuclear machines. This worm specifically targeted industrial control systems. It's believed this attack was meant to slow down Iran's nuclear program.
Big Data Collection Concerns
In 2013, documents were released that showed large-scale data collection by government agencies. These documents raised concerns about privacy. They suggested that some agencies might have used secret ways to access encrypted information. This led to public discussions about how much data governments collect.
Target and Home Depot Hacks
In 2013, attackers broke into Target Corporation's computers. They stole about 40 million credit card numbers. The next year, they also got into Home Depot's computers. There, they stole over 50 million credit card numbers. Both companies had received warnings but didn't act on them. These attacks could have been stopped by existing antivirus software.
Government Data Breach
In 2015, the US Office of Personnel Management found out it had been hacked. This attack happened over a year earlier. About 21.5 million employee records were stolen. This was one of the biggest government data breaches in US history. The stolen data included names, birth dates, addresses, and fingerprints.
Colonial Pipeline Attack
In June 2021, a cyberattack hit the Colonial Pipeline. This is the largest fuel pipeline in the U.S. The attack caused fuel shortages across the East Coast. This showed how cyberattacks can affect real-world services.
Government's Role in Cybersecurity
Governments play a role in cybersecurity. They create rules to help companies protect their systems and information. They also work to protect important national systems, like the power grid.
Some people believe the internet should be free from government rules. Others think governments need to do more to improve cybersecurity. They argue that companies might not fix problems without rules. Governments also discuss cybersecurity on a global level. They want to make sure new technologies don't harm people's rights or international peace.
Working Together Globally
Many groups around the world work together on cybersecurity.
- The Forum of Incident Response and Security Teams (FIRST) is a global group of computer security teams. Big companies like Apple and Microsoft are part of it.
- The Council of Europe helps protect against cybercrime.
- The Messaging Anti-Abuse Working Group (MAAWG) works to stop spam, viruses, and other messaging problems.
- The European Network and Information Security Agency (ENISA) works to improve network security in Europe.
In Europe, there's a rule called the General Data Protection Regulation (GDPR). It gives people the right to protect their personal data. It makes sure companies handle your information safely.
Cyber Warfare
There's a growing concern that the internet could become a new battlefield. This is called cyber warfare. It means wars could be fought using computer programs. These programs could disrupt or destroy important systems. This includes power, transportation, and communication networks. They could also disable military systems.
This has led to terms like cyberterrorism. Many countries now have special cyber forces. For example, the United States Cyber Command was created in 2009.
Careers in Cybersecurity
Cybersecurity is a fast-growing job field in IT. These jobs focus on protecting organizations from hacks and data breaches. Many companies need more cybersecurity experts. Jobs are growing fast in areas like finance, healthcare, and retail.
Here are some common cybersecurity job titles:
Cybersecurity Job Roles
- Security Analyst: This person finds weaknesses in software, hardware, and networks. They investigate security problems and suggest ways to fix them.
- Security Engineer: They watch for security incidents and help respond to them. They also work on new ways to make systems safer.
- Security Architect: This role designs the security systems for computers and networks. They make sure the overall plan is strong and safe.
- Chief Information Security Officer (CISO): This is a top manager who leads the whole information security team.
- Data Protection Officer (DPO): This person makes sure an organization follows data protection rules, like GDPR. They also help with training.
- Security Consultant/Specialist: These are experts who help protect computers, networks, and data from all kinds of attacks.
There are many ways to learn about cybersecurity. You can find student programs and online training.
Key Cybersecurity Terms
Here are some important words used in computer security:
- Access Authorization: This means only certain people can use a computer or service. It uses authentication like passwords.
- Anti-virus software: Programs that find and remove computer viruses and other malware.
- Applications: These are programs you use. It's best to only install trusted ones and keep them updated.
- Authentication: Making sure someone or something is who they say they are.
- Backups: Copies of your important files. Keep them in different places in case something happens to the originals.
- Confidentiality: Keeping information private and secret. Only authorized people should see it.
- Cryptography: Using codes to protect data. This makes it unreadable to anyone who shouldn't see it.
- Cyber attribution: Trying to find out who is behind a cyberattack.
- Cyberwarfare: Online conflicts between countries or groups. They use computers to attack systems.
- Data integrity: Making sure data is accurate and hasn't been changed without permission.

- Encryption: Turning information into a secret code. This protects it from being read by others.
- Endpoint security: Protecting devices like laptops and phones that connect to a network.
- Firewall: A system that blocks unwanted traffic from entering or leaving a network.
- Hacker: Someone who tries to break into computer systems.
- Honeypot: A fake computer system set up to attract and trap attackers. This helps learn their methods.
- Intrusion Detection System (IDS): Software that watches for suspicious activity on networks.
- Key logger: A type of spyware that records everything you type on your keyboard.
- Social Engineering: Tricking people to get secret information.
- Logic bomb: A hidden piece of malware that waits for a specific event to activate.
- Zero trust security: A security idea where no one is trusted by default. Everyone must prove who they are to get access.
A Brief History of Cybersecurity
Cybersecurity has been important for over 60 years, especially since the Internet became popular. In the 1970s and 1980s, computer security was mostly studied in universities. But as more computers connected online, computer viruses and network attacks started to appear. By the 2000s, organized attacks like distributed denial of service became common. This led to cybersecurity becoming a professional field.
In 1977, the "CIA triad" was introduced. This simple idea describes the main goals of security: keeping information confidential, maintaining its integrity, and making sure it's available.
Early computer threats were often from people inside an organization. They would get unauthorized access to files. One of the first computer worms, called Creeper, appeared in 1971. It was just an experiment. Later, in the 1980s, some German hackers were caught spying on US military networks.
In 1988, the Morris worm spread across the internet. It was one of the first widely known computer worms. In the 1990s, companies like Netscape started developing secure ways to browse the web, like SSL.
Government agencies also play a role in cybersecurity. They work to protect their own systems and gather information. Sometimes, tools developed for defense can end up being used by others. For example, in 2007, some countries used computer attacks to damage equipment in Iran. This led Iran to develop its own cyber defense.
See also
- Attack tree
- Bicycle attack
- CAPTCHA
- Center for Internet Security
- Cloud computing security
- Comparison of antivirus software
- Content Disarm & Reconstruction
- Content Security Policy
- Countermeasure (computer)
- Cyber insurance
- Cyber self-defense
- Cyberbiosecurity
- Cybersecurity information technology list
- Dancing pigs
- Data security
- Defense strategy (computing)
- Fault tolerance
- Hardware security
- Human–computer interaction (security)
- Identity management
- Identity-based security
- Information security awareness
- Internet privacy
- Internet safety
- Internet security
- IT risk
- IT security standards
- Cyber kill chain
- List of computer security certifications
- List of cyber warfare forces
- Open security
- Outline of computer security
- OWASP
- Physical information security
- Privacy software
- Security engineering
- Security through obscurity
- Software-defined perimeter
See also
 In Spanish: Seguridad informática para niños
In Spanish: Seguridad informática para niños